Are you facing an HTTP Flood DDOS Attack?
This guide will help you.
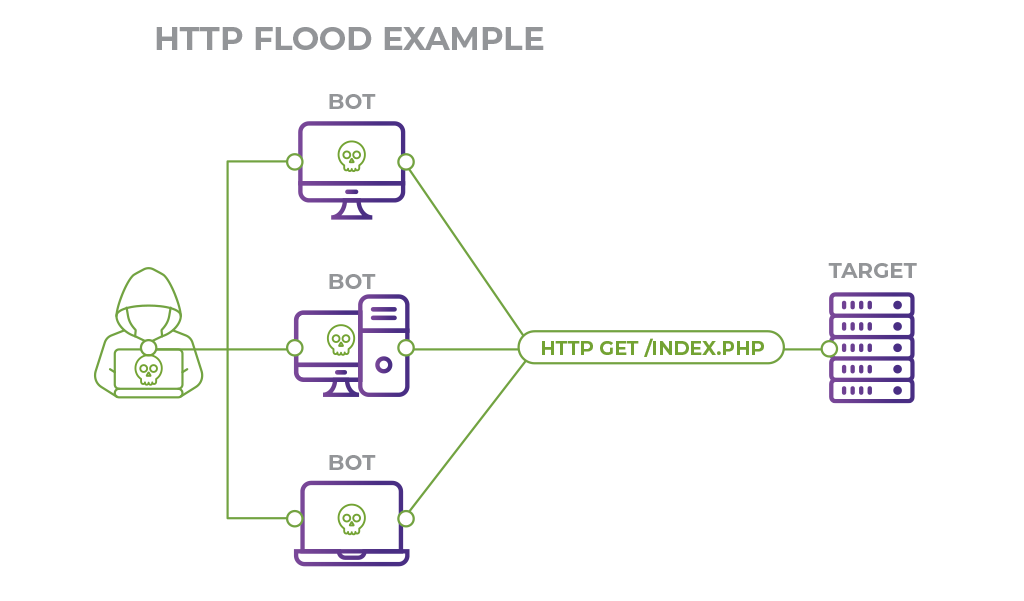
An HTTP flood DDoS attack utilizes what appear to be legitimate HTTP GET or POST requests to attack a web server or application. These flooding DDoS attacks often rely on a botnet, which is a group of Internet-connected computers that have been maliciously appropriated through the use of malware such as a Trojan Horse.
Here at Ibmi Media, as part of our Server Management Services, we regularly help our Customers to fix DDoS attacks.
In this context, we shall look into how to mitigate an HTTP Flood DDOS Attack.
Nature of HTTP flood DDoS attack?
An HTTP flood attack usually targets a server with HTTP requests. It is usually hard to recover from DDoS attacks. Hence, we find it very important to protect web servers against them.
It is a type of volumetric distributed denial-of-service (DDoS) attack that targets a server and saturate them with requests. Once the target is unable to respond to normal traffic, denial-of-service will occur for additional requests from actual users.
How does HTTP flood DDoS attack work ?
HTTP flood attacks are a type of "layer 7" DDoS attack. In order to achieve maximum efficiency, malicious actors will commonly employ or create botnets.
By utilizing many devices infected with malware, an attacker is able to leverage their efforts by launching a larger volume of attack traffic.
Generally, there are two varieties of HTTP flood attacks:
i. HTTP GET attack
Here, multiple computers or other devices coordinate to send multiple requests for images, files, or some other asset from a targeted server.
Once the target inundates with incoming requests and responses, denial-of-service will occur to additional requests from legitimate traffic sources.
ii. HTTP POST attack
Typically the server must handle an incoming form or request and push the data into a persistence layer, most often a database. This process is relatively intensive compared to the amount of processing power and bandwidth required to send the POST request.
They utilize the disparity in relative resource consumption. And send many post requests directly to a target server until its capacity is saturated and denial-of-service occurs.
How to mitigate HTTP Flood DDOS Attack ?
1. Setup captcha test to test whether the requesting machine is a bot or not.
2. Install Mod_security module.
It uses various protection rules to monitor the HTTP traffic and block suspicious/unwanted traffic, SQL injection, etc.
In addition, we can set custom protection rules and add them to the mod_security configuration file /usr/local/apache/conf/mod_security.conf.
In order to limit the maximum data that can post on a web application, we can tweak the following mod_security parameters:
SecRequestBodyLimit
SecRequestBodyNoFilesLimit3. Install mod_evasive Apache module
The mod_evasive Apache module tracks the IP addresses and pages requested to the Apache web server and blocks the traffic from that IP when the threshold reaches the page or site. As a result, the website displays 403 Forbidden errors.
Below are some of the mod_evasive parameters that we tweak in mod_evasive.conf file to prevent DDoS attacks:
DOSHashTableSize
DOSPageCount
DOSSiteCount
DOSPageInterval
DOSSiteInterval
DOSBlockingPeriod4. Install DDoS Deflate
It is an effective tool for mitigating DDoS attacks for a limited number of websites. It is a bash script that uses netstat to identify and ban IPs that open too many connections to the server.
DDoS Deflate runs the following command to check the number of connections.
netstat -ntu | awk ‘{print $5}’ | cut -d: -f1 | sort | uniq -c | sort -nOnce it exceeds the threshold limit, it will automatically block that IP on the server.
It is possible for us to tweak the threshold connection limit, the frequency at which the script runs, etc. In order to adjust these parameters, we can tweak the DDoS Deflate configuration file "/usr/local/ddos/ddos.conf".
5. Software firewall
Similarly, to prevent these attacks in Apache we need to tweak some parameters in the server firewall.
For example, in CSF, we enable and tweak parameters such as SYNFLOOD and PORTFLOOD to limit the connections on the Apache webserver port.
In the same way, we configure APF and iptables to mitigate DDoS.
For example, in iptables, we set rules to rate-limit the number of connections on Apache port 80.
iptables -A INPUT -p tcp –syn –dport 80 -m connlimit –connlimit-above 20 -j REJECT –reject-with tcp-resetSimilarly, if the number of connections exceeds the threshold, the server blocks the IP.
6. Install Fail2ban
Fail2ban is a good option to prevent DDoS attacks in Apache. It uses a list of regular expressions and checks against server logs.
Like the above methods, once connections exceed, it blocks such IP addresses in the firewall.
Similarly, Fail2ban uses jails to determine the severs they have to protect.
For example, we add the following code in fail2ban configuration file /etc/fail2ban/jail.local to enable Apache DDoS jail:
[apache]
enabled = true
port = http,https
filter = apache-auth
logpath = /var/log/apache2/*error.log
maxretry = 4
findtime = 500
ignoreip = 10x.12x.1xx.xx77. Tweak Apache Configuration
We can also tweak certain Apache configuration parameters like RequestReadTimeout, Timeout, KeepAliveTimeout, etc. to reduce the impact of the attacks.
For example, we can lower the KeepAliveTimeout parameter. Similarly, we tune MaxRequestWorkers directive to allow the server to handle a maximum number of simultaneous connections without running out of resources.
8. Sysctl based protection
We can tweak the values set for SYN_SENT, SYN_RECV, TIME_WAIT, and FIN_WAIT by modifying the below parameters in the /etc/sysctl.conf file:
net.ipv4.tcp_syncookies
net.ipv4.tcp_fin_timeout
net.ipv4.tcp_window_scaling
net.ipv4.tcp_sack9. Setup Load balancer
However, the best way is the use of load balancers such as HAProxy. In web servers, we also limit the number of connections per user, limit the HTTP request rate, etc.
[Need urgent help with the mitigation? We'd be happy to assist. ]
Conclusion
This article will guide you on how to recover from DDoS attacks. Basically, protecting the web server against #DDoS #attacks is important. You can apply these measures to mitigate the error from causing troubles.
DNS #flood is a type of Distributed Denial of Service (DDoS) attack in which the attacker targets one or more Domain Name System (#DNS) servers belonging to a given zone, attempting to hamper resolution of resource records of that zone and its sub-zones.
To prevent DDoS attacks:
1. Buy more bandwidth.
2. Build redundancy into your infrastructure.
3. Configure your network hardware against DDoS attacks.
4. Deploy anti-DDoS hardware and #software #modules.
5. Deploy a DDoS protection appliance.
6. Protect your DNS servers.
This article will guide you on how to recover from DDoS attacks. Basically, protecting the web server against #DDoS #attacks is important. You can apply these measures to mitigate the error from causing troubles.
DNS #flood is a type of Distributed Denial of Service (DDoS) attack in which the attacker targets one or more Domain Name System (#DNS) servers belonging to a given zone, attempting to hamper resolution of resource records of that zone and its sub-zones.
To prevent DDoS attacks:
1. Buy more bandwidth.
2. Build redundancy into your infrastructure.
3. Configure your network hardware against DDoS attacks.
4. Deploy anti-DDoS hardware and #software #modules.
5. Deploy a DDoS protection appliance.
6. Protect your DNS servers.