Website Iframe malware injection
This article covers methods to secure websites from iframe attacks. Iframes Bring Security Risks. If you create an iframe, your site becomes vulnerable to cross-site attacks. You may get a submittable malicious web form, phishing your users' personal data.
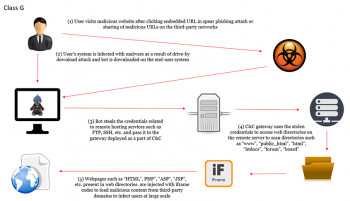
One of the most popular online attacks that happens all the time has to do with thousands of legitimate websites being hacked with the “Iframe code injection” attack resulting in Cross Site Scripting (XSS) or silent redirections to malicious websites.
This means that unsuspicious visitors get infected with a malware virus when they visit that legitimate websites.
What happens is that an “Iframe html code” is injected at the end (usually) of “index.php” or “index.html” files of the legitimate websites.
This “iframe” code embeds into the legitimate site a malicious code which installs a virus to the visitor’s PC or tries to steal sensitive information.
Some tips to clean the infection of your site:
1. First of all scan and clean your own computer which you use to connect to your site. The Trojan might be undetectable by some antivirus, so you better format the windows OS and install a fresh copy.
2. Change ALL your passwords and most importantly the FTP passwords and the website control panel passwords.
3. Download all files from your website and store them in a safe place on your PC to further analyze the infection.
4. If you have a recent clean backup of your website, upload the backup files and replace all current files.
5. If you don’t have a backup (shame on you!!) then edit all source code (html or PHP files) and search for <iframe> html commands inside the code. Delete the suspicious <iframe> and re-upload all html, php files to your website.
6. Download an antivirus tool which scans the website for <iframe> content.
If you use WordPress there are some great security plugins which scan your website's source code for infections and also protect the site with a firewall.
ICMP Flood Attack Methods to mitigate
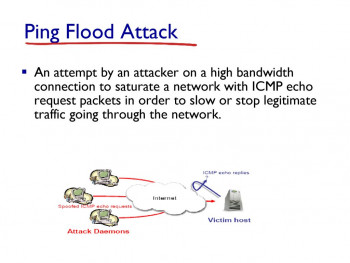
This article will guide you on methods to mitigate ICMP flood #attack. This is the type of Denial of Service (DoS) attack in which an attacker attempts to crash, destabilize, or freeze the targeted computer or service by sending malformed or oversized packets using a simple ping command.
Many network administrators feel that ICMP is a security risk, and should therefore always be blocked at the firewall. It is true that ICMP does have some security issues associated with it, and that a lot of #ICMP should be blocked.
But this is no reason to block all ICMP traffic!
To mitigate Ping flood attack:
1. Disabling a ping flood is most easily accomplished by disabling the ICMP functionality of the targeted router, computer or other device.
2. A network administrator can access the administrative interface of the device and disable its ability to send and receive any requests using the ICMP, effectively eliminating both the processing of the request and the Echo Reply.
3. The consequence of this is that all network activities that involve ICMP are disabled, making the device unresponsive to ping requests, traceroute requests, and other network activities.
Harden the security of Django
This article will guide you on steps to #harden the #security of #Django. We leveraged python-dotenv for handling secrets and settings.
Our sensitive mostly kept in settings.py file. We can protect that data using Python Decouple #Library. It is the library for separating parameters from the source code.
To make Django secure:
1. Use #SSL.
2. Change the URL.
3. Use 'django-admin-honeypot'.
4. Require stronger passwords.
5. Use two-factor authentication.
6. Use the latest version of Django.
7. Never run 'DEBUG' in production.
Smurf DDoS attack How to fix
In this article , you will learn the measures taken by our Support Experts to mitigate #Smurf #DDoS #attacks.
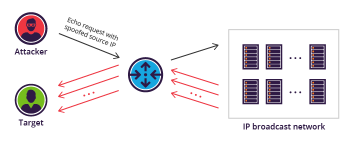
A Smurf attack is a form of a distributed denial of service (DDoS) attack that renders computer networks inoperable. The Smurf program accomplishes this by exploiting #vulnerabilities of the Internet Protocol (#IP) and Internet Control Message Protocols (#ICMP).
Smurf is a network layer distributed denial of service (DDoS) attack, named after the DDoS.Smurf malware that enables it execution.
1. DoS is one of the oldest forms of cyber extortion attack.
2. As the term indicates, distributed denial of service (DDoS) means it denies its service to a legitimate user.
3. Ping of death and teardrop attacks are examples of such attacks. Flooding: Sending too much data to the victim can also slow it down.
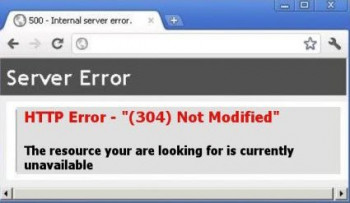
304 not modified error Steps to fix it
An #HTTP 304 not modified status #code means that the website you're requesting hasn't been updated since the last time you accessed it.
Basically, your browser will save (or cache) web #pages so it doesn't have to repeatedly download the same information. This is an attempt to speed up page delivery. However, if this happens to your site, #visitors could be prevented from accessing your #web pages.
24 7 365 hosting tech support
Whether you need technical support at any time of the day, With Ibmi Media, we give support remotely to our Customers. Also, we offer technical support, cloud computing, and website development and hosting support.
Our support team is available to assist you 24/7/365 with any hosting or WordPress problem. Get world-class support when you need it.