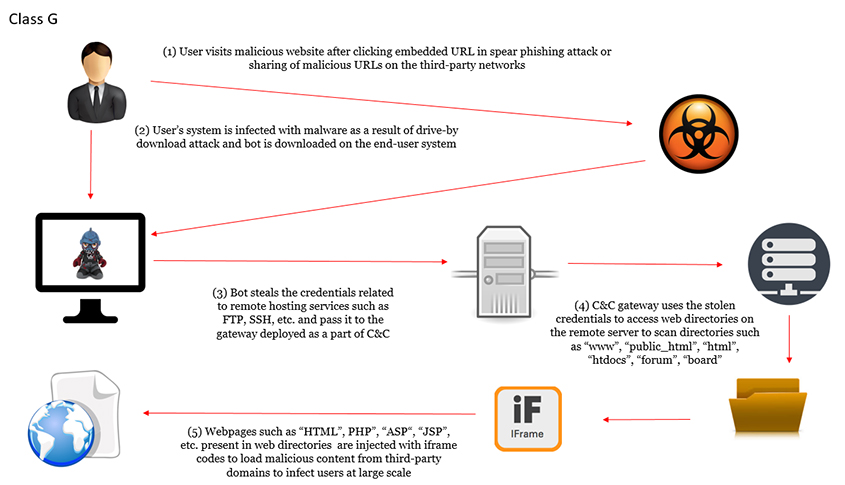
An iFrame injection is a very common cross-site scripting (or XSS) attack. It consists of one or more iFrame tags that have been inserted into a page or post's content and typically downloads an executable program or conducts other actions that compromise the site visitors' computers.
Securing a website from IFrame malware injection is quite important as it may later crash the complete website.
Here at Ibmi Media, as part of our Server Management Services, we regularly help our Customers to fix different website attacks.
In this context, we shall look into how to secure a website from iframe malware injection.
Nature of IFrame injection attack ?
In Iframe injection, the hackers inject or insert their IFrame codes to the website. Here, they may make use of the trojan malware.
Usually, here hackers target the index.html, index.php, default.php, or configuration.php pages.
When someone accesses a website, that is infected with malicious code, the browser will download that code (this is a trojan horse/spyware) from the URL present in the IFrame container.
Then all the visitors who visit the infected site will get infected with malicious malware.
How to secure Website From IFrame Malware Injection ?
Here, you will learn ways to secure websites from Iframe malware injection.
Recently, one of our clients contacted us saying that his site was blocked by Google due to some malware content on the website. On investigation, we found that the malware warning was due to the IFrame malware injection in some of the files on the site.
Here is how we remove the IFrame from the website:
i. Firstly, we verify whether there is a threat or not. For that, we scan the webpage or website using any antivirus tool that checks for <iframe> content.
If the result does not show any attacks, then the website is safe and we can ask Google for a review.
ii. However, if the website is infected then we start to remove the malware contents.
In order to get rid of the infections, we need to remove all the IFrame code out of our infected PHP or HTML files.
Steps to remove the IFrame infections ?
1. First, we scan and clean our own computer which we use to connect to our site. The Trojan might be undetectable by some antivirus. So better to format the windows OS and install a fresh copy.
2. We change ALL passwords including the FTP passwords and the website control panel passwords.
3. Also, we check the files on the server for the IFrame code using any tool and we remove it. We can download an antivirus tool that scans the website for <iframe> content.
If it is a WordPress website then there are some great security plugins available like Wordfence that will scan the website's source code for infections and also protect the site.
4. Clearing the CMS’s cache
5. Temporarily, we block access to the website.
6. Replacing the infected file with original files that we have during the last virus-free site backup. Changing the permission to 444 to avoid further injection.
7. If we do not have a backup, then we edit all source code (HTML or PHP files) and search for <iframe> HTML commands inside the code.
Delete the suspicious <iframe> and re-upload all HTML, PHP files to the website.
8. We recheck the files to see whether the IFrames exist or not.
9. Also, we clear our CMS’s cache once more.
10. We make sure to monitor the IFrame attack for some more days.
11. Lastly, we always keep a virus-free backup.
[Need urgent assistance with iframe-related queries? - We are here to help you. ]
Conclusion
This article covers methods to secure websites from iframe attacks. Iframes Bring Security Risks. If you create an iframe, your site becomes vulnerable to cross-site attacks. You may get a submittable malicious web form, phishing your users' personal data.
One of the most popular online attacks that happens all the time has to do with thousands of legitimate websites being hacked with the “Iframe code injection” attack resulting in Cross Site Scripting (XSS) or silent redirections to malicious websites.
This means that unsuspicious visitors get infected with a malware virus when they visit that legitimate websites.
What happens is that an “Iframe html code” is injected at the end (usually) of “index.php” or “index.html” files of the legitimate websites.
This “iframe” code embeds into the legitimate site a malicious code which installs a virus to the visitor’s PC or tries to steal sensitive information.
Some tips to clean the infection of your site:
1. First of all scan and clean your own computer which you use to connect to your site. The Trojan might be undetectable by some antivirus, so you better format the windows OS and install a fresh copy.
2. Change ALL your passwords and most importantly the FTP passwords and the website control panel passwords.
3. Download all files from your website and store them in a safe place on your PC to further analyze the infection.
4. If you have a recent clean backup of your website, upload the backup files and replace all current files.
5. If you don’t have a backup (shame on you!!) then edit all source code (html or PHP files) and search for <iframe> html commands inside the code. Delete the suspicious <iframe> and re-upload all html, php files to your website.
6. Download an antivirus tool which scans the website for <iframe> content.
If you use WordPress there are some great security plugins which scan your website's source code for infections and also protect the site with a firewall.
This article covers methods to secure websites from iframe attacks. Iframes Bring Security Risks. If you create an iframe, your site becomes vulnerable to cross-site attacks. You may get a submittable malicious web form, phishing your users' personal data.
One of the most popular online attacks that happens all the time has to do with thousands of legitimate websites being hacked with the “Iframe code injection” attack resulting in Cross Site Scripting (XSS) or silent redirections to malicious websites.
This means that unsuspicious visitors get infected with a malware virus when they visit that legitimate websites.
What happens is that an “Iframe html code” is injected at the end (usually) of “index.php” or “index.html” files of the legitimate websites.
This “iframe” code embeds into the legitimate site a malicious code which installs a virus to the visitor’s PC or tries to steal sensitive information.
Some tips to clean the infection of your site:
1. First of all scan and clean your own computer which you use to connect to your site. The Trojan might be undetectable by some antivirus, so you better format the windows OS and install a fresh copy.
2. Change ALL your passwords and most importantly the FTP passwords and the website control panel passwords.
3. Download all files from your website and store them in a safe place on your PC to further analyze the infection.
4. If you have a recent clean backup of your website, upload the backup files and replace all current files.
5. If you don’t have a backup (shame on you!!) then edit all source code (html or PHP files) and search for <iframe> html commands inside the code. Delete the suspicious <iframe> and re-upload all html, php files to your website.
6. Download an antivirus tool which scans the website for <iframe> content.
If you use WordPress there are some great security plugins which scan your website's source code for infections and also protect the site with a firewall.