Smurf is a network layer distributed denial of service (DDoS) attack, named after the DDoS.
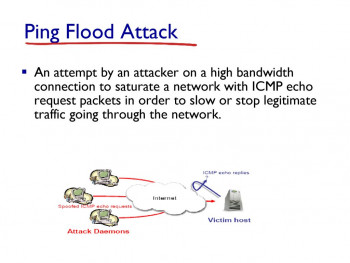
Smurf attacks are somewhat similar to ping floods, as both are carried out by sending a slews of ICMP Echo request packets.
Here at Ibmi Media, as part of our Server Management Services, we regularly help our Customers to mitigate smurf attacks.
In this context, we shall look into ways to prevent Smurf DDoS attack.
Nature of Smurf DDoS attack ?
A Smurf attack is a network layer distributed denial of service (DDoS) attack, named after the DDoS.Smurf malware.
These days Smurf DDoS attack is one of the most common forms of cyber-attacks that we need to take care of to secure our network.
Here, an attacker attempts to flood a targeted server with Internet Control Message Protocol (ICMP) packets.
Also, the attacker tries to make multiple requests with the spoofed IP address of the targeted device or networks resulting in high traffic on the target device.
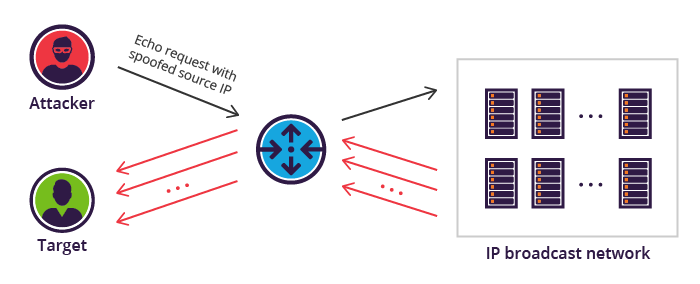
Smurf attacks often exploit characteristics of broadcast networks.
How does a Smurf attack work?
1. Initially, a ping (ICMP packets) is used to see if a device is operational, and to track the amount of time it takes for the message to go round trip from the source device to the target and back to the source.
2. Smurf malware builds a spoofed packet that contains the source address set to the real IP address of the targeted victim.
3. This packet is then sent to an IP broadcast address of a router or firewall which will send the request to every host device inside the broadcasting network.
4. This will increase the number of requests from the number of networked devices on the network.
5. All the devices which receive the request responds to the spoofed address of the target with an ICMP Echo Reply packet.
4. The target will end up receiving a huge number of ICMP Echo Reply packets resulting in denial-of-service to legitimate traffic.
Types of Smurf DDoS Attacks ?
Following are the two types of Smurf Attacks:
i. Basic Attack
A basic smurf attack occurs when we get ICMP request packet flood and high traffic as a result.
The packets contain a source address that is set to the broadcast address of the target’s network.
If the packets disperse correctly, every device that connects to the network on target it will reply to the ICMP request with an echo, resulting in a lot of traffic and possibly crashing the server.
ii. Advanced Attack
These start very similarly to a basic attack. The difference is that the echo-request will configure its source to respond to a third-party victim.
This third-party victim will then receive the echo request that originates from the targeted subnet.
How can a Smurf attack be mitigated?
1. First we can disable the IP broadcasting addresses at each network router and a firewall is one way to mitigate this attack.
In the older routers broadcasting is enabled by default.
2. After that we will try re-configuring the operating system to disallow ICMP responses to IP broadcast requests.
3. Re-configuring the perimeter firewall to disallow pings originating from outside the network.
[Facing Smurf DDoS attack? We are happy to help you! ]
Conclusion
In this article , you will learn the measures taken by our Support Experts to mitigate #Smurf #DDoS #attacks.
A Smurf attack is a form of a distributed denial of service (DDoS) attack that renders computer networks inoperable. The Smurf program accomplishes this by exploiting #vulnerabilities of the Internet Protocol (#IP) and Internet Control Message Protocols (#ICMP).
Smurf is a network layer distributed denial of service (DDoS) attack, named after the DDoS.Smurf malware that enables it execution.
1. DoS is one of the oldest forms of cyber extortion attack.
2. As the term indicates, distributed denial of service (DDoS) means it denies its service to a legitimate user.
3. Ping of death and teardrop attacks are examples of such attacks. Flooding: Sending too much data to the victim can also slow it down.
In this article , you will learn the measures taken by our Support Experts to mitigate #Smurf #DDoS #attacks.
A Smurf attack is a form of a distributed denial of service (DDoS) attack that renders computer networks inoperable. The Smurf program accomplishes this by exploiting #vulnerabilities of the Internet Protocol (#IP) and Internet Control Message Protocols (#ICMP).
Smurf is a network layer distributed denial of service (DDoS) attack, named after the DDoS.Smurf malware that enables it execution.
1. DoS is one of the oldest forms of cyber extortion attack.
2. As the term indicates, distributed denial of service (DDoS) means it denies its service to a legitimate user.
3. Ping of death and teardrop attacks are examples of such attacks. Flooding: Sending too much data to the victim can also slow it down.