Are you trying to enable OCSP stapling on Nginx?
This guide will help you.
In OCSP stapling, the server includes a current OCSP response for the certificate included (or "stapled") into the initial HTTPS connection. That removes the need for the browser to request the OCSP response itself. OCSP stapling is widely supported by modern browsers.
Here at Ibmi Media, as part of our Server Management Services, we regularly help our Customers to performing Nginx related queries.
In this context, we shall look into how to configure OCSP stapling on Nginx.
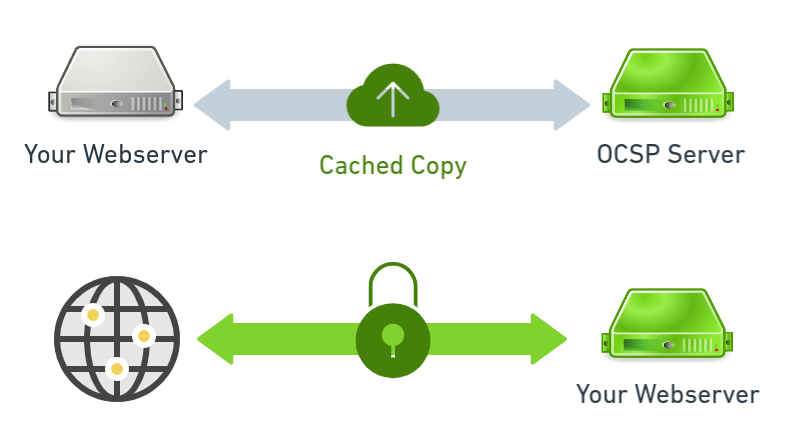
How does OCSP Stapling Works?
i. First, the webserver hosting the SSL certificate sends a query to the issuing CA’s server.
ii. Next, the issuing CA’s server responds with the OCSP status and a timestamp.
iii. From this point, whenever a client connects the server staples the OCSP response to the certificate when it’s presented during the handshake.
iv. The client verifies the signature on the timestamp to ensure it came from the issuing CA.
If the issue persists, the client's browser issues an error message.
Some Advantages of OCSP Stapling?
One of the biggest advantages of OCSP is performance speed. Also, the handshake is a process that can add a lot of latency to connections.
OCSP stapling can help speed up the authentication process by reducing the number of queries the client has to make when checking validity. As a result, it would make pages load quicker.
How to Enable OCSP stapling on Nginx?
The below steps will guide you on how enable OCSP stapling on Nginx where the Nginx version is 1.6.2.
1. Check the version of Nginx
Generally, Nginx supports OCSP stapling in 1.3.7+.
So to see which version of Nginx we are running, we run the following command:
nginx -v2. Check if OCSP stapling is enabled
a. In order to see if OCSP stapling is enabled or not, we run the following OpenSSL command:
openssl s_client -connect [yoursite.com]:443 -statusIf OCSP stapling is set, in the response, in the OCSP Response Data section. Then it should say something as below:
OCSP Response Status: successful (0x0)If OCSP stapling is not enabled, we won’t see any OCSP Response Data. So now we need to see if the Intermediate Certificate is properly installed or not.
b. Check that the Intermediate Certificate is properly installed
Before we can enable OCSP stapling on the Nginx server, we must properly install the Intermediate Certificate. Also, we check whether the connection to OCSP servers is working fine.
c. Furthermore, if the server is not sending the necessary intermediate certificate, we will need to configure it in the "ssl_certificate" line of the SSL configuration.
3. Configure your Nginx server to use OCSP Stapling
We follow the below instruction to enable OCSP stapling on the Nginx server after verifying that it supports OSCP stapling and can connect to the OCSP server.
a. First, we edit the website’s SSL configuration file.
Add the following directives INSIDE the "server { }" block:
ssl_stapling on;
ssl_stapling_verify on;
For example:
server
{
listen 443 ssl;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_certificate /etc/ssl/bundle.crt;
ssl_certificate_key /etc/ssl/your_domain_name.key;
ssl_stapling on;
ssl_stapling_verify on;
}b. (Optional) Add a DNS resolver for stapling
Now we add a DNS resolver for stapling so that the resolver defaults to Google’s DNS.
resolver 8.8.4.4 8.8.8.8;
In case, if we don’t add this line then the resolver defaults to the server’s DNS default.
c. Also, we check the configuration for errors with Ngnix. For that, we run the below command.
nginx -td. Finally, we reload the Nginx. For that, we run the below command.
systemctl restart nginx4. Verify that OCSP stapling is now enabled
To see if OCSP stapling is enabled, we run the below OpenSSL command.
openssl s_client -connect [yoursite.com]:443 -statusIf OCSP stapling is enabled, in the response, in the OCSP Response Data section, it should say the following:
OCSP Response Status: successful (0x0)[Need any further assistance with Nginx queries? – We are here to help you.]
Conclusion
This article will guide you on the steps to configure OCSP stapling on the Nginx server.
This article will guide you on the steps to configure OCSP stapling on the Nginx server.