Trying to secure sites in IIS?
This guide will help you.
Microsoft Internet Information Server (IIS) is widely used in the enterprise, despite a less-than-stellar reputation for security.
It is an effective way to secure a site is by doing IIS hardening when configured correctly.
Here at Ibmi Media, as part of our Server Management Services, we regularly help our Customers to perform Server hardening tasks.
In this context, we shall look into how to do this easily.
Ways to secure sites in IIS ?
One of the main reasons for site infections or defacing on a Windows VPS Server is poor file security or poor configuration choices when it comes to how IIS should access file content. The effective way to prevent this is to start with a secure site.
How to add the Site to IIS ?
Follow the steps provided below;
1. Here, we will look into the process of Secure a Site in IIS via the interface.
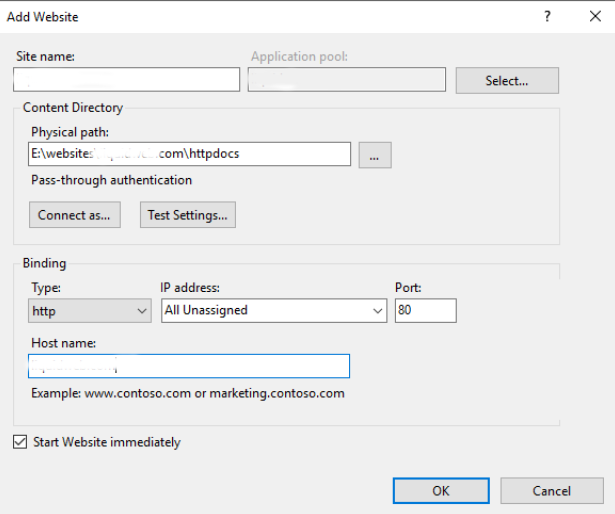
i. To add a website in IIS (Internet Information Services), we open up the IIS Manager, right-click on Sites, and select Add Website.
You need to take note of the follow as this is what they signify.
a. Site name- Recommend using the domain name as the “Site name” for easy identification.
b. Physical path- Provide the path to where the website content is located.
c. Configuration options under “Connect as-and “Test Settings do not need to alter*.
ii. Next, we set the Anonymous User. To do this, we change the associated Anonymous user and make a few security changes on the website’s content folder.
So, In IIS, we select the new site on the left > in the main window double click on Authentication > Select Anonymous Authentication > Then click the Edit button on the right action bar.
iii. In addition, when it comes to hosting multiple domains, we switch IUSR account for sites, and select “Application pool identity” and click OK. Or manually create a user on the system for each site.
iv. We set Folder Permissions in IIS. Basically, the “ApplicationPoolIdentity” user has very few permissions. So we set up proper security settings for website files.
To do this, browse through your file system and find the folder with the site’s files. Then, we right-click on the folder and go to properties. In the properties interface, select the Security tab. Next, we set up correct security permissions on the folder. Also, we disable inheritance. To do this, we click on Advanced, then click on Disable inheritance.
2. Now, let's look into the process of Secure a Site in IIS via the interface.
Note that the above steps can be achieved via Powershell. In this case, it can be implemented on a Windows Server 2012 or newer server through Powershell.
So do the following;
i. Initially, we simply fill out the first two variables with the domain name and the path to the content.
ii. Then, we run the rest of the PowerShell commands to set up the site in IIS and configure folder permissions as below;
[String]$Domain = ‘<domain_Name>’
[String]$Root = ‘<path_to_your_content>’
Import-Module WebAdministrationiii. Next, we create App pool & Website
New-WebAppPool -Name $Domain
New-Website -Name $Domain -HostHeader $Domain -PhysicalPath $Root -ApplicationPool $Domain
Set-WebConfigurationProperty -Filter system.webServer/security/authentication/anonymousAuthentication -Location $Domain -PSPath MACHINE/WEBROOT/APPHOST -Name userName -Value ''
iv. Optionally add www. Binding
New-WebBinding -Name $Domain -HostHeader www.$Domain -ErrorAction
v. Then, we remove inheritance (copy)
$ACL = Get-ACL $Root
$ACL.SetAccessRuleProtection($True,$True) | Out-Null
$ACL.Access | ?{ !(($_.IdentityReference -eq 'NT AUTHORITY\SYSTEM') -or ($_.IdentityReference -eq 'BUILTIN\Administrators')) } | %{ $ACL.RemoveAccessRule( $_ ) } | Out-Null
$ACL | Set-ACL
vi. We add IIS user permissions
$ACL = Get-ACL $Root
$acl.SetAccessRuleProtection($False, $True)
$Rule = New-Object System.Security.AccessControl.FileSystemAccessRule("IIS AppPool\$Domain", "ReadAndExecute", "ContainerInherit, ObjectInherit", "None", "Allow")
$acl.AddAccessRule($Rule)
$acl | Set-Acl
This is the process!
Steps to increase security for your IIS web apps and servers?
To enhance IIS server security, apply the following tips.
1. Analyze dependencies and uninstall unneeded IIS modules after upgrading.
If you plan on upgrading from a previous version of IIS, be forewarned that your previous installation’s state information and metabase will be carried over to the new install. Be sure to disable and/or uninstall any unused IIS components and features to minimize the web server’s attack surface. Even if you haven't upgraded, ensure that only required modules are present.
2. Properly configure web server user/group accounts
IIS features built-in user and group accounts dedicated to the web server. So for example, separate system and application administrator accounts can be created for more granular-level access. System administrators can therefore give application administrators the rights to make application-level configuration changes without the need to grant them administrative access to the server. These accounts should be audited on a ongoing basis to ensure they are configured securely.
3. Use IIS 7's CGI/ISAPI Restrictions
CGI and ISAPI are two common ways to build upon IIS—either for generating dynamic content or for extending IIS’ native capabilities. Unfortunately, CGI files (.exe) and ISAPI extensions (.dll) are also commonly exploited in web attacks and should be restricted if not in use. For example, if you’re using PHP or ColdFusion to create dynamic content with IIS, use of CGI and other ISAPI extensions may not be needed. Like IIS modules, these configurations should be uninstalled unless they are being specifically used.
4. Configure HTTP Request Filtering Options
UrlScan was an extension that functioned as a security tool for restricting HTTP requests. UrlScan functionality is now built right into IIS, and should be configured appropriately. Potentially harmful HTTP requests are prevented from reaching the server through rule-based filtering. These options are critical for mitigating threats like SQL injections, among others, and should be used in conjunction with your IIS-based web application.
5. Use Dynamic IP Restrictions
Dynamic IP address restrictions use a requestor’s IP addresses and domain name to determine whether or not to restrict access. This is essentially a whitelist—"allowUnlisted"—that IIS uses to prevent unauthorized access. So in the event of Denial of Service (DoS) and brute force attacks, IIS’ Dynamic IP Restrictions (DIPR) module can temporarily block IP addresses making unusual requests.
6. Incorporate URL Authorization In Your Application
URL authorization grants access to URLs within an IIS application based on user names and roles, as opposed to server or system accounts. This makes it easier to restrict content based on group membership. URL authorization rules can be associated with a server, site, or application.
7. Use Encrypted Forms-Based Authentication
Forms-based authentication allows for the management of client registration and authentication at the application level, as opposed to on the Windows account level. Because this authentication mechanism passes form values as clear text, SSL must be installed to encrypt sensitive data.
8. Use Application Pool Identities
This feature of IIS enables more granular security by running application pools under unique accounts, bypassing domain or local account creation/management. By using a low-privileged account—namely, ApplicationPoolIdentity—multiple distinct sets of anonymous website content can be isolated without having to create a unique account for each website.
9. Isolate/Segregate Web Applications
By using a combination of the above IIS features, you can achieve more secure isolation and segregation for your web applications. In general, the following security recommendations should be taken into consideration:
i. Each application pool should be assigned to a single website.
ii. The application pool should be assigned to a dedicated user.
iii. Anonymous user identities should be set up to use the application pool.
10. Fix Critical IIS Vulnerabilities
Finally, critical IIS vulnerabilities should be patched or remediated. Like any Microsoft updates, staying on top of patches and service packs helps ensure that your server is as protected as possible. Most exploits target vulnerabilities that are over a year old and have patches released, so a little regular maintenance goes a long way. Patches should first be deployed in a test environment before production, and each update should be considered and approved if possible before being authorized in the organization.
[Need urgent assistance with server hardening tasks? – We're available 24*7. ]
Conclusion
This article will guide you on the process to #secure sites in IIS to prevent site infections or defacing on a #Windows Server include poor file security or poor #configuration.
In conclusion, the modular nature of #IIS allows for more granular control over web server resources and #security. However, this can either make your #web #applications more or less secure—depending on the person or group responsible for security.
This article will guide you on the process to #secure sites in IIS to prevent site infections or defacing on a #Windows Server include poor file security or poor #configuration.
In conclusion, the modular nature of #IIS allows for more granular control over web server resources and #security. However, this can either make your #web #applications more or less secure—depending on the person or group responsible for security.