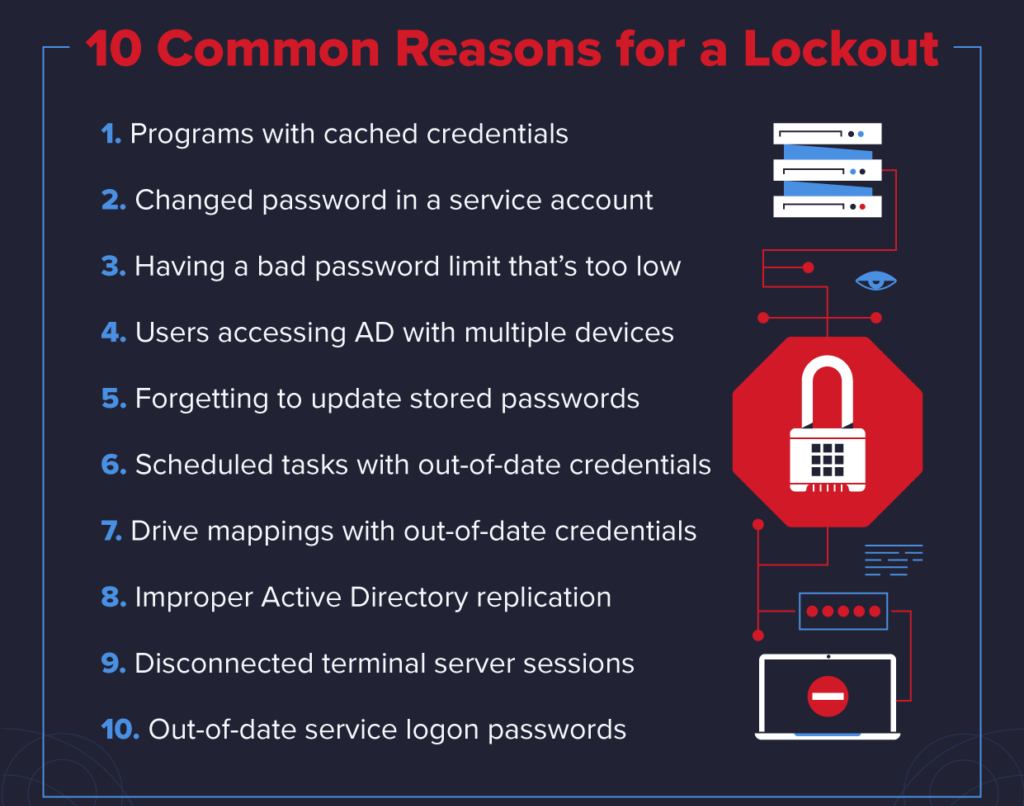
Account lockouts are a headache for system administrators, and they happen a lot in Active Directory (AD). Research shows that account lockouts are the biggest single source of calls to IT support desks.
It is quite easy to find the source of Account Lockouts in the Active Directory domain.
Here at Ibmi Media, as part of our Server management Services, we regularly help our Customers to perform Windows related queries.
In this context, we shall look into steps to find the source of Account Lockouts.
Why account lockouts in the Active directory ?
Active Directory auditing is a process where it collects the data about the AD objects and analyzes and reports on that data, in order to determine the overall health of the directory. This process is very important as it ensures the security of the IT environment.
However, one of the most common issue Active Directory auditors face is finding the source of account lockouts.
In case, if any user gets locked out due to any reason then the password modifications, may result in downtime. Also, it can often be a time-consuming process to get the AD account re-enabled.
Generally, the account gets locked out due to repeatedly entering bad passwords.
How to Identify the source of Account Lockouts in Active Directory ?
Now let's take a look at how our Support Experts identify locked out accounts and find the source of Active Directory account lockouts.
1. Searching for the DC (Domain Controller) having the PDC Emulator Role
Generally, the DC (Domain Controller) with the PDC emulator role will capture every account lockout event with an event ID 4740.
We run the below cmdlet to search the domain controller having the role of a PDC emulator.
<Get-AdDomain>.pdcemulator2. Looking for the Event ID 4740
Next, we open the event log viewer of the DC. Then we go to the security logs and search for Event ID 4740.
3. Applying Appropriate Filters in Place
In order to generate a more customized report, we can apply suitable filters. For instance, we can search for a lockout that occurred in the last hour or last 12 hours and find the recent lockout source of a particular user.
4. Finding out the Locked Out Account Event
Now we shall click on the Find button in the Actions pane. Then we enter the user whose account is locked out.
5. Open the Event Report to see the Source of the Locked Out account
Finally, now we can find the name of the user account in the "Account Name" section. Also, we can find the lockout location as well in the 'Caller Computer Name' field.
[Need urgent assistance with Windows queries? – We are here to help you. ]
Conclusion
This article will guide you on steps to find the source of Account Lockouts in the Active Directory #domain.
The most common underlying cause for #AD account lockouts, beyond users forgetting their password, is a running application or background service on a device that is authenticating with stale credentials.
To Track Source of Account Lockouts in #Active #Directory:
1. Search for the #DC (Domain Controller) having the PDC Emulator Role.
2. Look for the Event ID 4740.
3. Put Appropriate Filters in Place.
4. Find Out the Locked Out Account Event Whose Information is Require.
5. Open the #Event Report, to Find the Source of the Locked Out account.
This article will guide you on steps to find the source of Account Lockouts in the Active Directory #domain.
The most common underlying cause for #AD account lockouts, beyond users forgetting their password, is a running application or background service on a device that is authenticating with stale credentials.
To Track Source of Account Lockouts in #Active #Directory:
1. Search for the #DC (Domain Controller) having the PDC Emulator Role.
2. Look for the Event ID 4740.
3. Put Appropriate Filters in Place.
4. Find Out the Locked Out Account Event Whose Information is Require.
5. Open the #Event Report, to Find the Source of the Locked Out account.