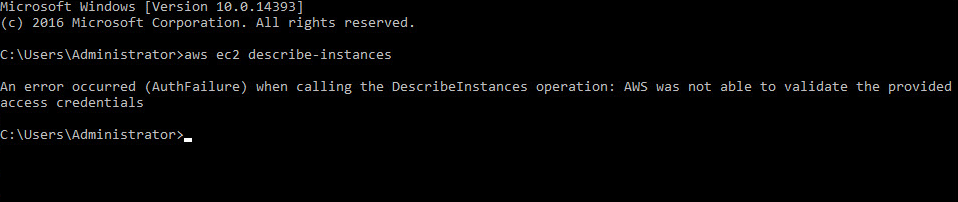
The instances for your AWS account is handled by the describe-instances command. Most AWS users have experienced error such as "AWS was not able to validate the provided access credentials".
We have helped customers fixed AWS related issues as part of our Server Support Services.
In this context, we shall look into the causes and how to get rid of this error.
More about the error AWS was not able to validate the provided access credentials
This error is triggered by different factors such as;
i. An outdated version format for session tokens in relation with the AWS security token service (AWS STS) could be the reason for this error it only supports an updated version. By default, the new AWS Regions is not enabled to use the updated AWS STS format.
ii. When the AWS CLI is of Boto type. Boto helps in collecting data in a specialized location $HOME/.boto.
iii. The Authentication tokens Timestamp should be considered as an invalid date or time will trigger an error "AWS was not able to validate the provided access credentials".
iv. The format of the file can also result to issues.
How to solve AWS was not able to validate the provided access credentials
We shall describe briefly about the best way to go about resolving this AWS issue.
i. The choice of the version of the Session tokens.
it should be considered being that tokens generated from Regional endpoints comes with the new version format which will work correctly in all AWS Regions. Therefore is is best to use the Regional STS endpoints.
ii. The Authentication tokens Timestamps needs to be accurate as possible.
Via the AWS ssh CLI, you can configure the aws via the command below;
aws configure
This will show some errors. If this is the case, it is better to correct the Date and time by synching with the standard time if that would work.
To set the time, run the command below;
sudo date -s "$(wget -qSO- --max-redirect=0 google.com 2>&1 | grep Date: | cut -d' ' -f5-8)Z"
sudo ntpclient -s -i 1 -l -d -h 0.amazon.pool.ntp.org //This will sync the clock for VM/instance
In a situation where NTPD is available in the system, you can run the following command to complete setup;
datesudo service ntpd stopsudo ntpdate time.nist.govsudo service ntpd startntpstat
This will help to synchronize with NTP.
iii. Using Boto in relation with the AWS CLI
Another method of solving this error ensure that the login credential is accurate. you can check it via the command below and the output will be displayed as per your aws information;
cat ~/.boto
[Credentials]aws_access_key_id=MY*OLD*ACCESS*KEYaws_secret_access_key=MY*OLD_SECRET*ACCESS*KEYNeed Support in solving AWS errors? Get the help you need here.
Conclusion
Comprehensive method of fixing AWS was not able to validate the provided access credentials
Comprehensive method of fixing AWS was not able to validate the provided access credentials