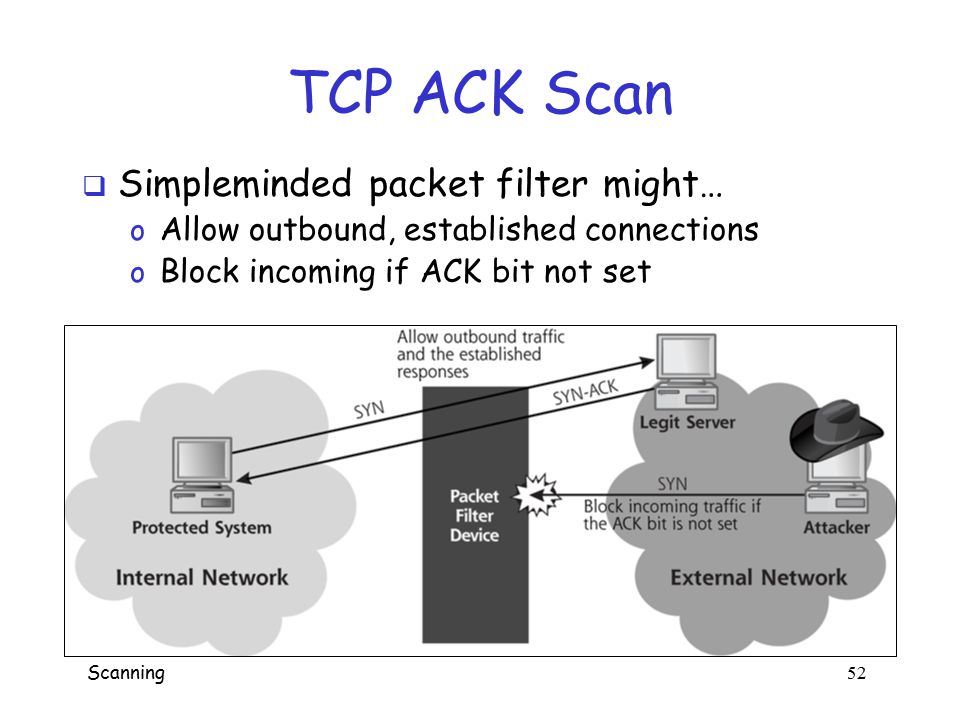
Are you trying to mitigate ACK scan DOS attack?
This guide is for you.
ACK scans are generally used to identify ports or hosts that may be filtered to resist any other form of scanning.
Here, a target system is presented with a packet with the ACK flag set with a sequence number of zero to an interesting port (such as, port 25).
An adversary uses TCP ACK segments to gather information about firewall or ACL configuration.
Attackers scan our router or send unwanted traffic/requests like SYN, ACK, FIN to specific UDP/TCP Port. Sometimes, they also send continuous unwanted traffic into particular open port/s.
This can crash our router and make it out of service.
Here at Ibmi Media, as part of our Server Management Services, we regularly help our Customers to prevent any form of DOS attack.
In this context, we shall look into ways to mitigate DDoS attacks.
Nature of ACK scan DOS attack ?
A target system is presented with a packet with the ACK flag set with a sequence number of zero to an interesting port.
Generally, if the sequence number is not zero, there is a violation of TCP rules associated with that parameter.
And the target sends back an RST. The presence of the RST provides an attacker a good indication that the host is alive but behind some form of filtering like a firewall, a router, or even some proxies.
A TCP ACK segment when sent to a closed port or sent out-of-sync to a listening port, the expected behavior is for the device to respond with an RST. This helps the attacker to get an idea about the type of firewall.
When combined with SYN techniques an attacker will get a clear picture of the types of packets that get through to a host and can understand the firewall rule-set.
ACK scanning, when combined with SYN scanning, also allows the adversary to analyze whether a firewall is stateful or non-stateful.
Rules for detecting ACK scan DOS attack:
You can apply the following rules;
alert tcp 172.16.16.0/24 any -> 172.16.17.0/24 any (flags:A; ack:0; msg: “Potential Ack Scan”; sid: 10001;)or
alert tcp 172.16.16.0/24 any -> 172.16.17.0/24 any (flags:AR; msg: “Ack and RST detected-Potential Ack Scan”; sid: 10002;)In the first rule, the assumption is that the Acknowledgment flag will be set and the sequence value will be set to “0”. This will make the target return an “RST”.
The second rule looks for the existence of an “RST” with the Acknowledgment flag set rather than looking for the existence of a zero-sequence value. The existence of these two flags together simultaneously can also be an indicator of an ACK scan being used for reconnaissance purposes, or “firewalking”.
Any SYN-ACK responses are possible connections: an RST(reset) response means the port is closed, but there is a live computer here. No responses indicate SYN is filtered on the network.
An attacker can scan the router or send unwanted traffic/request like SYN,ACK,FIN to specific UDP/TCP Port.
Generally, if the router is accessible from outside of the network, the attacker can access it by brute force.
A typical Probe response is given below:
Probe Response - Assigned State
-------------------------------------------------------------------
TCP RST response - unfiltered
No response received (even after retransmissions) - filtered
ICMP unreachable error - filteredAn example of a typical ACK scan:
# nmap -sA -T4 <target>
Starting Nmap ( http://nmap.org )
Nmap scan report for target
Not shown: 994 filtered ports
PORT STATE SERVICE
22/tcp unfiltered ssh
25/tcp unfiltered smtp
53/tcp unfiltered domain
70/tcp unfiltered gopher
80/tcp unfiltered http
113/tcp unfiltered auth
Nmap done: 1 IP address (1 host up) scanned in 4.01 secondsHow to mitigate ACK scan DOS attack ?
1. Set up a firewall to filter scan attempts.
We can use the following commands to filter scan attempts with iptables:
iptables -A INPUT -p tcp –tcp-flags SYN,ACK SYN,ACK -m state –state NEW -j DROP
iptables -A INPUT -p tcp –tcp-flags ALL NONE -j DROP
iptables -A INPUT -p tcp –tcp-flags SYN,FIN SYN,FIN -j DROP
iptables -A INPUT -p tcp –tcp-flags SYN,RST SYN,RST -j DROP
iptables -A INPUT -p tcp –tcp-flags ALL SYN,RST,ACK,FIN,URG -j DROP
iptables -A INPUT -p tcp –tcp-flags FIN,RST FIN,RST -j DROP
iptables -A INPUT -p tcp –tcp-flags ACK,FIN FIN -j DROP
iptables -A INPUT -p tcp –tcp-flags ACK,PSH PSH -j DROP
iptables -A INPUT -p tcp –tcp-flags ACK,URG URG -j DROP2. Reset the IP if it’s dynamic. Just turn the router off for the DHCP lease time or spoof a different MAC address.
3. Appropriate rules can be applied to DROP PKT like: burst limit/rate, Source limit, destination limit, connection limit, length, etc.
We can use the following IPtables commands for this:
$ sudo iptables --append INPUT --source 123.123.123.123 --jump DROPor
# iptables -A INPUT -m state --state NEW -j DROP
[Need urgent assistance to mitigate ACK scan DOS attack? We are happy to help you. ]
Conclusion
This article will guide you on how the ACK scan DOS #attack works as well as methods to mitigate this.
A port scan can help an attacker find a weak point to attack and break into a computer system.
Just because you've found an open port doesn't mean you can attack it. But, once you've found an open port running a listening service, you can scan it for vulnerabilities.
Denial of service attack (DOS) is an attack against computer or network which reduces, restricts or prevents accessibility of its system resources to authorized users. The network of Bots is called botnet.
A Fraggle Attack is a denial-of-service (#DoS) attack that involves sending a large amount of spoofed UDP traffic to a router's broadcast address within a network.
It is very similar to a Smurf Attack, which uses spoofed ICMP traffic rather than UDP traffic to achieve the same goal.
Common DoS attacks:
1. Buffer overflow attacks – the most common DoS attack.
2. ICMP flood – leverages misconfigured network devices by sending spoofed packets that ping every computer on the targeted network, instead of just one specific machine.
3. SYN flood – sends a request to connect to a server, but never completes the handshake.
To prevent port scan attacks:
i. Install a Firewall: A firewall can help prevent unauthorized access to your private network.
ii. TCP Wrappers: TCP wrapper can give administrators the flexibility to permit or deny access to the servers based on IP addresses or domain names.
This article will guide you on how the ACK scan DOS #attack works as well as methods to mitigate this.
A port scan can help an attacker find a weak point to attack and break into a computer system.
Just because you've found an open port doesn't mean you can attack it. But, once you've found an open port running a listening service, you can scan it for vulnerabilities.
Denial of service attack (DOS) is an attack against computer or network which reduces, restricts or prevents accessibility of its system resources to authorized users. The network of Bots is called botnet.
A Fraggle Attack is a denial-of-service (#DoS) attack that involves sending a large amount of spoofed UDP traffic to a router's broadcast address within a network.
It is very similar to a Smurf Attack, which uses spoofed ICMP traffic rather than UDP traffic to achieve the same goal.
Common DoS attacks:
1. Buffer overflow attacks – the most common DoS attack.
2. ICMP flood – leverages misconfigured network devices by sending spoofed packets that ping every computer on the targeted network, instead of just one specific machine.
3. SYN flood – sends a request to connect to a server, but never completes the handshake.
To prevent port scan attacks:
i. Install a Firewall: A firewall can help prevent unauthorized access to your private network.
ii. TCP Wrappers: TCP wrapper can give administrators the flexibility to permit or deny access to the servers based on IP addresses or domain names.