Here at Ibmi Media, we sometimes get requests to disable NTLM Authentication in Windows Domain and enable Kerberos instead for our customers.
In essence, NTLM (NT LAN Manager) is a basic Microsoft authentication protocol and is in use since Windows NT.
However, some tools such as Responder can capture NTLM data sent over the network and use them to access the network resources.
As a part of Server Management Services, we help to fix such Customer's requests by following some simple process.
The need to disable NTLMv1 Authentication in Windows Domain?
Windows 2000 Microsoft introduced a more secure Kerberos authentication protocol.
The NTLM (generally, it is NTLMv2) is still widely in use for authentication on Windows domain networks.
We recommend disabling NTLMv1 and NTLMv2 protocols and use Kerberos due to the following reasons:
1. NTLM has very weak encryption
2. NTLM stores password hash in the memory of the LSA service, which can be extracted using different tools and then used by attackers.
3. The absence of mutual authentication between a server and a client will result in data interception attacks
4. It will allow unauthorized access to network resources.
Version NTLMv2 uses more secure encryption algorithms and allows for preventing popular NTLM attacks.
NTLMv1 and LM authentication protocols are disabled by default starting with Windows 7/Windows Server 2008 R2.
In this case, it is recommended to disable NTLM Authentication in Windows Domain.
[Need further assistance with Windows tasks? We are here for you!]
How to Configure GPO to Force NTLMv2 in Windows Domain?
In order to disable NTLM Authentication in Windows Domain, it is necessary to ensure that we are not using a vulnerable version – NTLMv1.
Our network will have a number of legacy devices or services that will be using NTLMv1 authentication instead of NTLMv2 or Kerberos.
Therefore, you must ensure that NTLM and LM protocols are prohibited to be in use only for authentication in the domain.
This is so because some attackers can use special requests to receive a response to an NTLM/LM request.
To Set the preferred authentication type using the domain (or local) policy, follow the steps below:
1. Open the Group Policy Management Editor (gpmc.msc)
2. Edit the Default Domain Policy.
3. And go to the GPO section Computer Configurations
4. Select Policies
5. And then take Security Setting from Windows Settings
6. Then choose Local Policies -> Security Options
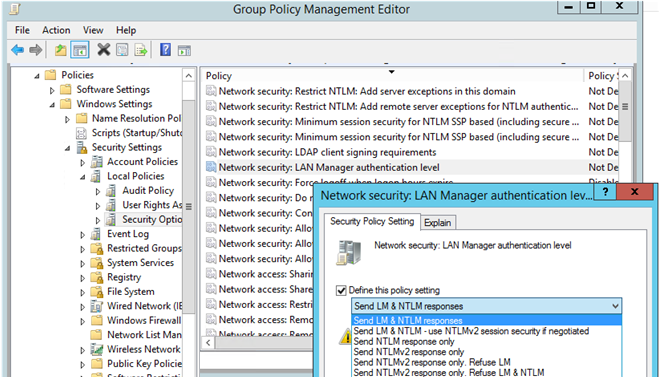
7. And find the policy Network Security: LAN Manager authentication level.
There are 6 options in the policy settings:
a. Send LM & NTLM response
b. Send LM & NTLM responses – use NTLMv2 session security if negotiated
c. Send NTLM response only
d. Send NTLMv2 response only
e. Send NTLMv2 response only. Refuse LM
f. Send NTLMv2 response only. Refuse LM& NTLM.
The policies of using NTLM authentication are given in the order of their security improvement.
By default, Windows 7 and newer OSes use the option Send NTLMv2 response only.
NTLMv2 can be used if the Kerberos protocol did not work, for some operations in workgroups.
You can change the policy value to the most secure 6 option: "Send NTLMv2 response only. Refuse LM & NTLM".
If we configure this setting on domain controllers, it will reject all LM and NTLMv1 requests.
What are the steps to disable NTLMv1 through the registry?
In order to disable NTLM Authentication in Windows Domain through the registry, simply follow the given steps below:
1. Create a DWORD parameter with the name LmCompatibilityLevel
2. And set the value 0-5 in the registry key HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Lsa.
(Value 5 corresponds to the policy option “Send NTLMv2 response only. Refuse LM NTLM”.)
Do not forget to apply this policy to your domain controllers.
The main risk of disabling NTLM is the potential usage of legacy or incorrectly configured applications that can still use NTLM authentication.
We will have to configure them in a special way to switch to Kerberos.
[Need help in Installing Software of your Ubuntu Linux Server? We are available to help you here !]
How to Enable NTLM Authentication Audit Logging?
Before we can completely disable NTLM in our domain and switching to Kerberos, we must ensure that there are no apps left in the domain that require and use NTLM authentication.
To track accounts or apps that are using NTLM authentication, you can enable audit logging policies using GPO.
Steps to enable audit logging policies using GPO?
1. Go to Configuration -> Windows Settings.
2. Then take Security Settings and select Local Policy.
3. Take the Security Options section, find and enable the Network Security: Restrict NTLM: Audit NTLM authentication in this domain policy.
4. And set its value to Enable all.
5. In the same way, enable the policy Network Security: Restrict NTLM: Audit Incoming NTLM Traffic and set its value to Enable auditing for domain accounts.
Steps to check events of using NTLM authentication
The events of using NTLM authentication appear in the Application and Services Logs. So do;
1. Go to Services Logs
2. Microsoft -> Windows
3. Take NTLM section of the Event Viewer.
You can analyze the events on each server or collect them to the central Windows Event Log Collector.
After we find out the users and applications that are using NTLM in the domain we need to switch them to use Kerberos (possibly using SPN).
We need to use the DNS name of the server instead of its IP address for Kerberos authentication.
The apps that cannot use Kerberos can be added to the exceptions. This will allow them to use NTLM authentication, even if it is disabled at the domain level.
How to Restrict NTLM in Active Directory Domain?
The authentication without NTLM will work differently for each application in our domain, we can add user accounts to the "Protected Users" domain group.
Members of this security group can authenticate only using Kerberos. After verifying this we can completely disable NTLM Authentication in the Windows domain.
We can use the Network Security: Restrict NTLM: NTLM authentication in this domain policy.
The policy has 5 options:
a. Disable: the policy is disabled (NTLM authentication is allowed in the domain)
b. Deny for domain accounts to domain servers: the domain controllers deny NTLM authentication attempts for all servers under the domain accounts, and the "NTLM is blocked" error appears
c. Deny for domain accounts: the domain controllers prevent NTLM authentication attempts for all domain accounts, and the "NTLM is blocked" error appears
d. Deny for domain servers: NTLM authentication requests are forbidden for all servers unless the server name is on the exception list in the “Network security: Restrict NTLM: Add server exceptions for NTLM authentication in this domain” policy
e. Deny all: the domain controllers block all NTLM requests for all domain servers and accounts.
[Are you looking for help to disable NTLM on Windows server? We are available to help you today !]
Conclusion
This article will guide you step by step on how to disable NTLM authentication which makes the Windows domain less vulnerable.
This article will guide you step by step on how to disable NTLM authentication which makes the Windows domain less vulnerable.