Are you trying to test RPC ports with PowerShell ?
This guide is for you.
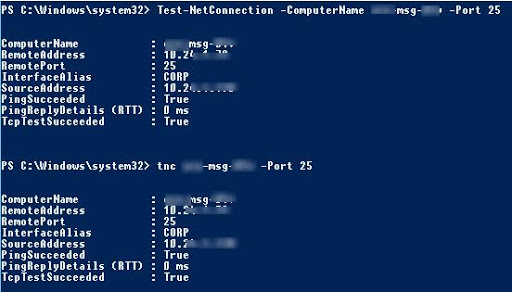
There's a PowerShell cmdlet for that, Test-NetConnection. With the -Port option, this cmdlet will do a quick TCP three-way handshake on the remote system to confirm that the service is available and reports back if it succeeded or not.
Here at Ibmi Media, as part of our Server Management Services, we regularly help our Customers to perform RPC related queries.
In this context, we shall look into the steps to identify RPC ports in use by capturing content from Dos commands like PortQRY.exe
How to go about Testing RPC ports with PowerShell ?
RPC communication is one of the tougher firewall problems. With RPC, we will get a range of ports from 49152 to 65535.
In general, there are default rules on firewalls, WAN accelerators, and the various devices that traffic hops through to get to its destination. Hence, they do not always work as we plan.
For example, RPC works like the concierge desk at a hotel. We walk up, ask the desk for information about services at the hotel. In this scenario, the person at the desk is RPC Endpoint Mapper on port 135. They direct us to the services that are listening on the ephemeral ports.
In order for RPC to work at the remote server, these checks must pass:
i. The display name “Remote Procedure Call (RPC)” must be running. This also has the service name of “RpcSs” and its path to execute is “C:\Windows\system32\svchost.exe -k rpcss”.
ii. Allow inbound port TCP-135 (in Windows firewall, endpoint firewall, and network firewalls).
iii. Outbound random ports ranging from 1022-5000 and 49152-65535 must also be permitted.
iv. Inbound port TCP-445 for SMB (RPC dependency) must be open.
[Having troubles with the RPC checklist? We are available 24*7. ]
How to get the RPC ports ?
We can troubleshoot this type of network connectivity using SysInternals PortQry.exe utility, which can be downloaded from the Microsoft website.
To begin, run the following command to query the RPC Port Mapper on the remote machine. It will return the ports in the ephemeral range that the machine is actively listening on for RPC services:
Portqry.exe -n 169.254.0.10 -e 135
Querying target system called:
169.254.0.10
Attempting to resolve IP address to a name…
IP address resolved to DC1.contoso.com
querying…
TCP port 135 (epmap service): LISTENING
Using ephemeral source port
Querying Endpoint Mapper Database…
Server’s response:
UUID: d95afe70-a6d5-4259-822e-2c84da1ddb0d
ncacn_ip_tcp:169.254.0.10[49664]
UUID: 50abc2a4-574d-40b3-9d66-ee4fd5fba076
ncacn_ip_tcp:169.254.0.10[64555]
UUID: 897e2e5f-93f3-4376-9c9c-fd2277495c27 Frs2 Service
ncacn_ip_tcp:169.254.0.10[64528]
UUID: 367abb81-9844-35f1-ad32-98f038001003
ncacn_ip_tcp:169.254.0.10[64502]
UUID: c9ac6db5-82b7-4e55-ae8a-e464ed7b4277 Impl friendly name
ncacn_ip_tcp:169.254.0.10[49668]
UUID: 12345778-1234-abcd-ef00-0123456789ac
ncacn_ip_tcp:192.168.0.242[49668]To check the ephemeral ports on which the server is listening, we look for any lines that have “ip_tcp” in them. The ports are in brackets at the end of the line.
This is where we will get a focused list of listening ports from the RPC server to query and validate connectivity. In the example above, ports 49664, 64555, 64502, and 49668 are listening. Note that 49668 is on the list twice.
Once we have the full list put together, we can feed the list of ports back into PORTQRY.EXE to validate that they are reachable over the network.
Furthermore, to check the ports, we execute the below script in PowerShell:
# This Sample Code is provided for the purpose of illustration only and is not intended to be used in a production environment.
# THIS SAMPLE CODE AND ANY RELATED INFORMATION ARE PROVIDED “AS IS” WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE IMPLIED WARRANTIES OF MERCHANTABILITY AND/OR
# FITNESS FOR A PARTICULAR PURPOSE.
#
#
# Script queries port 135 to get the listening ephemeral ports from the remote server
# and verifies that they are reachable.
#
#
# Usage: RPCCheck -Server YourServerNameHere
#
#
# Note: The script relies on portqry.exe (from Sysinternals) to get port 135 output.
# The path to portqry.exe will need to be modified to reflect your location
#
Param(
[string]$Server
)
# WORKFLOW QUERIES THE PASSED ARRAY OF PORTS TO DETERMINE STATUS
workflow Check-Port {
param ([string[]]$RPCServer,[array]$arrRPCPorts)
$comp = hostname
ForEach -parallel ($RPCPort in $arrRPCPorts)
{
$bolResult = InlineScript{Test-NetConnection -ComputerName $Using:RPCServer -port $Using:RPCPort _
-InformationLevel Quiet}
If ($bolResult)
{
Write-Output “$RPCPort on $RPCServer is reachable”
}
Else
{
Write-Output “$RPCPort on $RPCServer is unreachable”
}
}
}
# INITIAL RPC PORT
$strRPCPort = “135”
# MODIFY PATH TO THE PORTQRY BINARY IF NECESSARY
$strPortQryPath = “C:\Sysinternals”
# TEST THE PATH TO SEE IF THE BINARY EXISTS
If (Test-Path “$strPortQryPath\PortQry.exe”)
{
$strPortQryCmd = “$strPortQryPath\PortQry.exe -e $strRPCPort -n $Server”
}
Else
{
Write-Output “Could not locate Portqry.exe at the path $strPortQryPath”
Exit
}
# CREATE AN EMPTY ARRAY TO HOLD THE PORTS RETURNED FROM THE RPC PORTMAPPER
$arrPorts = @()
# RUN THE PORTQRY COMMAND TO GET THE EPHEMERAL PORTS
$arrQuryResult = Invoke-Expression $strPortQryCmd
# CREATE AN ARRAY OF THE PORTS
ForEach ($strResult in $arrQuryResult)
{
If ($strResult.Contains(“ip_tcp”))
{
$arrSplt = $strResult.Split(“[“)
$strPort = $arrSplt[1]
$strPort = $strPort.Replace(“]”,””)
$arrPorts += $strPort
}
}
# DE-DUPLICATE THE PORTS
$arrPorts = $arrPorts | Sort-Object |Select-Object -Unique
# EXECUTE THE WORKFLOW TO CHECK THE PORTS
Check-Port -RPCServer $Server -arrRPCPorts $arrPortsThe output will look similar to:
Testing RPC Dynamic Ports on SERVER01.KIMCONNECT.COM:
—————————————————-
5722: reachable
49159: reachable
49234: reachable
49155: reachable
49242: reachable
49240: reachable
49153: reachable
49154: reachable
49152: reachableMake sure to install PortQry. PortQry.exe is a Free solution and we can download it from www.sysinternals.com.
We will have to tell the script where the PortQry.exe binary is located by modifying the path on this line of the script: $strPortQryPath = “C:\Sysinternals”.
Finally, the script requires PowerShell v4 since it was written to use WorkFlow and Test-NetConnection, which requires PowerShell v3 & PowerShell v4 respectively.
[Stuck with RPC ports Setup? We are here for you!]
Conclusion
This article will guide you on how to go about pinging available RPC ports with PowerShell and #Sysinternals tools and we can test #RPC #ports with #PowerShell.
In #Windows, do this by typing "cmd" in the search box in the Start Menu and clicking the command prompt icon. In the command prompt window, type "telnet" followed by a space, then an IP address or domain name followed by another space, and then the port number.
This article will guide you on how to go about pinging available RPC ports with PowerShell and #Sysinternals tools and we can test #RPC #ports with #PowerShell.
In #Windows, do this by typing "cmd" in the search box in the Start Menu and clicking the command prompt icon. In the command prompt window, type "telnet" followed by a space, then an IP address or domain name followed by another space, and then the port number.