Are you trying to set up OCSP stapling on Apache?
This guide is for you.
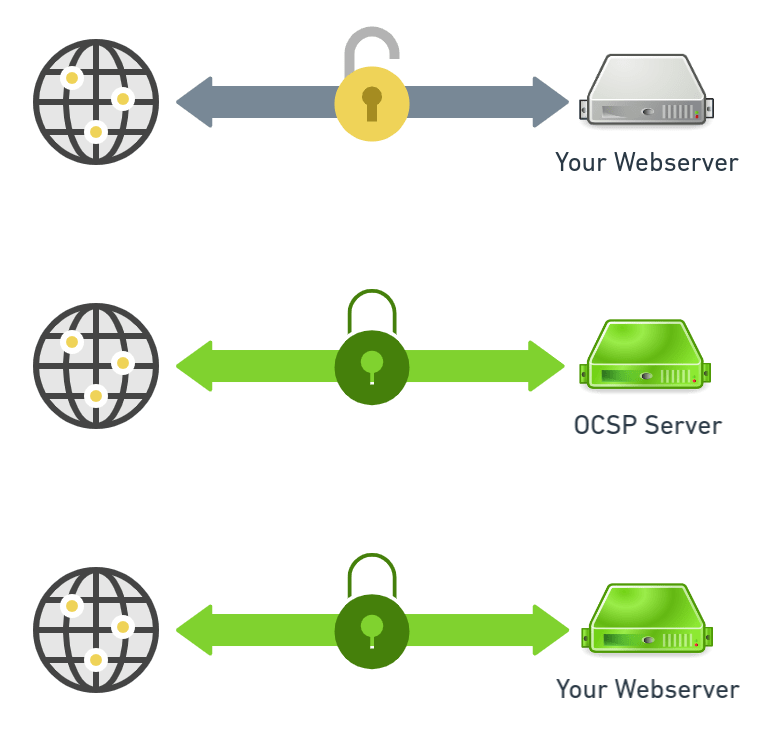
OCSP Stapling is a TLS extension that enables the web server to cache Certificate Revocation status information and not placing the onus on the web client to make the request directly with the Certificate Authority (CA).
Here at Ibmi Media, as part of our Server Management Services, we regularly help our Customers to perform Apache related configuration tasks.
In this context, we shall look into how to configure OCSP stapling on Apache.
How does OCSP Stapling Works ?
OCSP stapling is a more efficient way to handle the verification of certificate information. When a user attempts to visit the site, the digitally time-stamped response is then "stapled" with the TLS/SSL handshake via the Certificate Status Request extension response.
It works as follows:
i. First, the webserver hosting the SSL certificate sends a query to the issuing CA’s server.
ii. Next, the issuing CA’s server responds with the OCSP status and a timestamp.
iii. From this point, whenever a client connects the server staples the OCSP response to the certificate when it’s presented during the handshake.
iv. The client verifies the signature on the timestamp to ensure it came from the issuing CA.
If there is an issue, the client's browser issues an error message.
How to enable OCSP stapling on Apache HTTP SERVER ?
To enable OCSP stapling on Apache, follow the process below.
1. Check for OCSP stapling support on Apache
OCSP stapling is supported on Apache HTTP Server where version >=2.3.3
We run the following command to check the version of the apache installation.
apache2 -v
httpd -v2. Retrieve the CA bundle
Now, we retrieve the root CA and intermediate CA’s certificate in PEM format. Then we save them in a single file. This is for StartSSL’s Root and Intermediate CA certificates.
cd /etc/ssl
wget -O - https://www.startssl.com/certs/ca.pem https://www.startssl.com/certs/sub.class1.server.ca.pem | tee -a ca-certs.pem> /dev/nullIf the CA provides certificates in DER format then we convert them to PEM. For example DigiCert provides certificates in DER format. To download them and convert to PEM we run the following commands:
cd /etc/ssl
wget -O - https://www.digicert.com/CACerts/DigiCertHighAssuranceEVRootCA.crt | openssl x509 -inform DER -outform PEM | tee -a ca-certs.pem> /dev/null
wget -O - https://www.digicert.com/CACerts/DigiCertHighAssuranceEVCA-1.crt | openssl x509 -inform DER -outform PEM | tee -a ca-certs.pem> /dev/null3. Configuring OCSP Stapling on Apache
Now we shall configure the OCSP stapling.
First, we edit the SSL virtual hosts file by running the below command.
sudo nano /etc/apache2/sites-enabled/example.com-ssl.confThen we place these lines inside the <VirtualHost></VirtualHost> directive.
SSLCACertificateFile /etc/ssl/ca-certs.pem
SSLUseStapling onAlso, we specify a cache location outside <VirtualHost></VirtualHost> in the same file.
SSLStaplingCache shmcb:/tmp/stapling_cache(128000)Then we do a configtest to check for errors.
apachectl -tAfter that, we reload if Syntax OK is displayed.
service apache2 reloadWe access the website on IE (on Vista and above) or Firefox 26+ and check the error log.
tail /var/log/apache2/error.logIf the file defined in the SSLCACertificateFile directive is missing, a certificate an error similar to the following is displayed.
[Fri Jan 08 23:36:44.055900 2021] [ssl:error] [pid 1491:tid 139921007208320] AH02217: ssl_stapling_init_cert: Can't retrieve issuer certificate!
[Fri Jan 08 23:36:44.056018 2021] [ssl:error] [pid 1491:tid 139921007208320] AH02235: Unable to configure server certificate for staplingIf no such errors are displayed proceed to the final step.
How to Test OCSP Stapling on Apache ?
Finally, we test if the OCSP stapling is working or not by running the below command.
echo QUIT | openssl s_client -connect ibmimedia.com:443 -status 2> /dev/null | grep -A 17 'OCSP response:' | grep -B 17 'Next Update'The output of the above command will explain if the webserver responded with OCSP data.
[Need urgent assistance with Apache configuration tasks? – We are here to help you.]
Conclusion
This article will guide you on how to configure OCSP stapling on the Apache server.
To Check if #OCSP #stapling is enabled:
Go to https://www.digicert.com/help and in the Server Address box, type in your server address (i.e. www.ibmimedia.com). If OCSP stapling is enabled, under #SSL Certificate has not been revoked, to the right of OCSP Staple, it says Good.
To Configure your Apache server to use OCSP Stapling:
1. Edit your site's #VirtualHost SSL configuration.
2. Add the following line INSIDE the <VirtualHost></VirtualHost> block: SSLUseStapling on.
3. Check the configuration for errors with the Apache Control service. Apachectl -t.
4. Reload the Apache service. service apache2 reload.
This article will guide you on how to configure OCSP stapling on the Apache server.
To Check if #OCSP #stapling is enabled:
Go to https://www.digicert.com/help and in the Server Address box, type in your server address (i.e. www.ibmimedia.com). If OCSP stapling is enabled, under #SSL Certificate has not been revoked, to the right of OCSP Staple, it says Good.
To Configure your Apache server to use OCSP Stapling:
1. Edit your site's #VirtualHost SSL configuration.
2. Add the following line INSIDE the <VirtualHost></VirtualHost> block: SSLUseStapling on.
3. Check the configuration for errors with the Apache Control service. Apachectl -t.
4. Reload the Apache service. service apache2 reload.