Are you facing a Memcached DDOS attack?
This guide will help you.
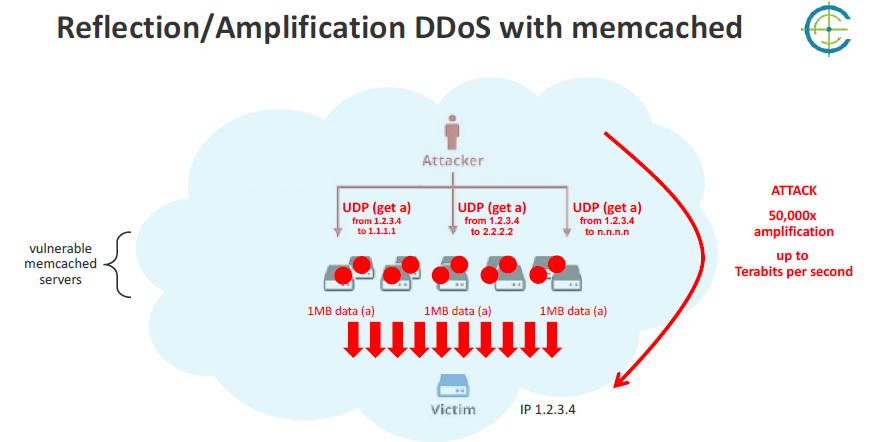
Memcached Distributed Denial of Service (DDoS) attack is a cyber attack aimed at Memcached, a database caching system designed to speed up websites and networks. It works by flooding a website or application with traffic to crash the servers.
Most of the time the vulnerable Memcached service is there by accident. We can find out if the server is under this attack by analyzing the bandwidth usage pattern.
Here at Ibmi Media, as part of our Server Management Services, we regularly help our Customers to resolve DDoS related attack.
In this context, we shall look into ways to mitigate Memcached DDOS attack.
Nature of Memcached DDOS attack ?
Memcached is just one service or process that runs on a server. Most of the time the vulnerable Memcached service is there by accident.
Attackers exploit Memcached reflection vulnerabilities to launch large denial-of-service attacks against target organizations.
If we analyze the bandwidth usage pattern, we can find if the server is vulnerable to this attack.
How to resolve Memcached DDOS attack ?
1. Disable UDP
We have to make sure to disable UDP support if unnecessary. By default, Memcached has UDP support enabled, potentially leaving a server vulnerable.
2. Firewall Memcached servers
Firewalling Memcached servers from the Internet helps system administrators to use UDP for Memcached if necessary without exposure.
3. Prevent IP spoofing
Preventing IP spoofing is a larger solution. However, It is not easy to implement by any particular system administrator It requires transit providers to not allow any packets to leave their network that has a source IP address originating outside the network.
In other words, if all major transit providers implemented this type of filtration, spoofing-based attacks would disappear overnight.
4. Develop software with reduced UDP responses
Another possible method is to remove the amplification factor to any incoming request. If the response data sent as a result of a UDP request is smaller than or equal to the initial request, amplification is no longer possible.
How to Disable UDP ?
Furthermore, let us see how our Support Experts disable UDP in detail.
i. For Memcached services on CentOS and Fedora servers, we can adjust the service parameters by editing the /etc/sysconfig/memcached file with vi.
For instance:
#netstat -plunt | grep memcached
tcp 0 0 0.0.0.0:11211 0.0.0.0:* LISTEN 1916/memcached
tcp6 0 0 :::11211 :::* LISTEN 1916/memcached
udp 0 0 0.0.0.0:11211 0.0.0.0:* 1916/memcached
udp6 0 0 :::11211 :::* 1916/memcachedii. To secure this we need to disable the Memcache listening to UDP port by editing the Memcached conf:
vi /etc/sysconfig/memcachediii. Similarly, to make Memcached listen to 127.0.0.1 and disable UDP we need to add the below line in /etc/sysconfig/memcached:
/etc/sysconfig/memcached
OPTIONS=”-l 127.0.0.1 -U 0″iv. Eventually, save and close the file.
v. Then we restart the Memcached service to apply changes:
sudo service Memcached restartvi. To verify that Memcached is currently bound to the local interface and listen only for TCP, we run:
netstat -plunt | grep memcached
tcp 0 0 127.0.0.1:11211 0.0.0.0:* LISTEN 1946/memcached
[root@server1 /]# netstat -plunt | grep memcached
tcp 0 0 127.0.0.1:11211 0.0.0.0:* LISTEN 11985/memcached[Still, stuck with this DDOS attack? We'd be happy to resolve them for you. ]
Conclusion
This article will guide you on methods to mitigate Memcached DDOS attacks which occur mostly by accident. To mitigate this attack, you can Disable #UDP, #Firewall #Memcached servers, and so on.
DoS attack is a denial of service attack where a computer is used to flood a server with TCP and UDP packets. A DDoS attack is where multiple systems target a single system with a DoS attack. The targeted network is then bombarded with packets from multiple locations.
DDoS attacks are illegal under the Computer Fraud and Abuse Act. Starting a DDoS attack against a network without permission is going to cost you up to 10 years in prison and up to a $500,000 fine.
There are three essential security measures that all small businesses should take to protect themselves from #DDoS #attacks: Use a web application firewall (#WAF): The absolute best way to prevent a DDoS attack is through the use of a WAF that blocks bad traffic and prevents DDoS attacks from accessing your web server.
A Denial-of-Service (#DoS) attack is an attack meant to shut down a machine or network, making it inaccessible to its intended users. DoS attacks accomplish this by flooding the target with traffic, or sending it information that triggers a crash.
Different DDoS attack method:
1. UDP flood.
2. ICMP (Ping) flood.
3. SYN flood.
4. Ping of Death.
5. Slowloris.
6. NTP Amplification.
7. HTTP flood.
This article will guide you on methods to mitigate Memcached DDOS attacks which occur mostly by accident. To mitigate this attack, you can Disable #UDP, #Firewall #Memcached servers, and so on.
DoS attack is a denial of service attack where a computer is used to flood a server with TCP and UDP packets. A DDoS attack is where multiple systems target a single system with a DoS attack. The targeted network is then bombarded with packets from multiple locations.
DDoS attacks are illegal under the Computer Fraud and Abuse Act. Starting a DDoS attack against a network without permission is going to cost you up to 10 years in prison and up to a $500,000 fine.
There are three essential security measures that all small businesses should take to protect themselves from #DDoS #attacks: Use a web application firewall (#WAF): The absolute best way to prevent a DDoS attack is through the use of a WAF that blocks bad traffic and prevents DDoS attacks from accessing your web server.
A Denial-of-Service (#DoS) attack is an attack meant to shut down a machine or network, making it inaccessible to its intended users. DoS attacks accomplish this by flooding the target with traffic, or sending it information that triggers a crash.
Different DDoS attack method:
1. UDP flood.
2. ICMP (Ping) flood.
3. SYN flood.
4. Ping of Death.
5. Slowloris.
6. NTP Amplification.
7. HTTP flood.