Are you trying to mitigate NTP amplification attack?
This guide is for you.
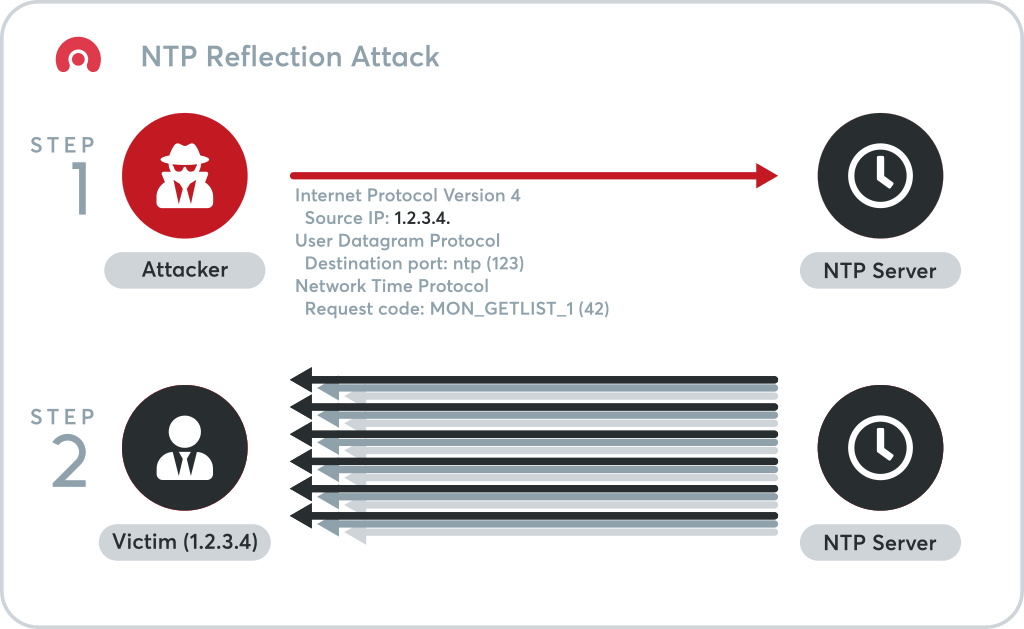
NTP amplification is a type of Distributed Denial of Service (DDoS) attack in which the attacker exploits publicly-accessible Network Time Protocol (NTP) servers to overwhelm the targeted with User Datagram Protocol (UDP) traffic.
The NTP server responds by sending the list to the spoofed IP address.
This renders the target and its surrounding infrastructure inaccessible to regular traffic.
Here at Ibmi Media, as part of our Server Management Services, we regularly help our Customers to resolve DOS related attacks.
In this context, we shall look into the steps to mitigate this attack.
How does an NTP amplification attack work?
The Network Time Protocol mainly allows internet-connected devices to synchronize their internal clocks. Also, it serves an important function in internet architecture.
An attacker can exploit the monlist command enabled on some NTP servers and will be able to multiply their initial request traffic, resulting in a large response. By default, this command is enabled on older devices and responds with the last 600 source IP addresses of requests which have been made to the NTP server.
We can break down an NTP amplification attack into four steps:
1. First, the attacker uses a botnet to send UDP packets with spoofed IP addresses to an NTP server. Here the NTP server has its monlist command enabled. The spoofed IP address on each packet points to the real IP address of the victim.
2. Next, each UDP packet makes a request to the NTP server using its monlist command, resulting in a large response.
3. The server will then respond to the spoofed address with the resulting data.
4. The IP address of the target receives the response and the surrounding network infrastructure becomes overwhelmed with the deluge of traffic, resulting in a denial-of-service.
As a result of the attack, any legitimate traffic coming from valid servers seems to be an attack. Also, mitigating this sort of attack traffic without blocking real NTP servers from legitimate activity is difficult.
Because UDP packets do not require a handshake, the NTP server will send large responses to the targeted server without verifying that the request is authentic.
Methods to mitigate NTP amplification attack ?
Now let's see some of the steps which our Support Experts follow to mitigate this issue.
1. Disable monlist – reduce the number of NTP servers that support the monlist command.
In order to overcome the monlist vulnerability is to disable the command. By default, all versions of the NTP software prior to version 4.2.7 is vulnerable. By upgrading an NTP server to 4.2.7 or above, the command is disabled which automatically patches the vulnerability.
2. Source IP verification – stop spoofed packets leaving the network.
The UDP requests sent by the attacker’s botnet must have a source IP address spoofed to the victim’s IP address. In order to reduce the effectiveness of UDP-based amplification attacks is for internet service providers (ISPs) to reject any internal traffic with spoofed IP addresses. If a packet is being sent from inside the network with a source address that makes it appear as it originated outside the network, it’s likely a spoofed packet and can be dropped.
3. On a Linux platform, the command "ntpdc" will query existing NTP servers for monitoring data.
If the system is vulnerable to exploitation, it will respond to the "monlist" command in interactive mode.
By default, most modern UNIX and Linux distributions allow this command to be used from localhost, but not from a remote host. We run the below command to test for monlist support:
/usr/sbin/ntpdc <remote server>
monlistAlso, in order to disable this functionality on a public-facing NTP server, add the “noquery” directive to the “restrict default” line in the system’s ntp.conf, as shown below:
restrict default kod nomodify notrap nopeer noquery4. We leverage the global scrubbing network, which scales on-demand to absorb and deflect multi-10Gbps DDoS threats.
5. Using proxy that ensures filtering of DDoS traffic outside of the client’s network, where it can’t cause any harm to its target.
[Still not able to mitigate the NTP amplification attack? – We are here to help you. ]
Conclusion
This article will guide you on steps to mitigate this #NTP amplification attack. An Amplification Attack is any attack where an attacker is able to use an amplification factor to multiply its power. Examples of #amplification #attacks include Smurf Attacks (ICMP amplification), Fraggle Attacks (#UDP amplification), and DNS Amplification.
DNS flood is a type of Distributed Denial of Service (#DDoS) attack in which the attacker targets one or more Domain Name System (#DNS) servers belonging to a given zone, attempting to hamper resolution of resource records of that zone and its sub-zones.
To harden your DNS server:
1. Audit your DNS zones. First things first.
2. Keep your DNS servers up-to-date.
3. Hide BIND version.
4. Restrict Zone Transfers.
5. Disable DNS recursion to prevent DNS poisoning attacks.
6. Use isolated DNS servers.
7. Use a DDOS mitigation provider.
8. Two-Factor Authentication.
This article will guide you on steps to mitigate this #NTP amplification attack. An Amplification Attack is any attack where an attacker is able to use an amplification factor to multiply its power. Examples of #amplification #attacks include Smurf Attacks (ICMP amplification), Fraggle Attacks (#UDP amplification), and DNS Amplification.
DNS flood is a type of Distributed Denial of Service (#DDoS) attack in which the attacker targets one or more Domain Name System (#DNS) servers belonging to a given zone, attempting to hamper resolution of resource records of that zone and its sub-zones.
To harden your DNS server:
1. Audit your DNS zones. First things first.
2. Keep your DNS servers up-to-date.
3. Hide BIND version.
4. Restrict Zone Transfers.
5. Disable DNS recursion to prevent DNS poisoning attacks.
6. Use isolated DNS servers.
7. Use a DDOS mitigation provider.
8. Two-Factor Authentication.