Are you facing ACK flood DDoS attack?
This guide is for you.
An ACK flood attack is when an attacker attempts to overload a server with TCP ACK packets. Like other DDoS attacks, the goal of an ACK flood is to deny service to other users by slowing down or crashing the target using junk data.
When attackers attempt to overload a server with TCP ACK packets, it results in an ACK flood attack.
Here at Ibmi Media, as part of our Server Management Services, we regularly help our Customers to fix DDoS related attacks.
In this context, we shall look into how ACK flood DDoS attack works.
Nature of ACK flood DDoS attack ?
An ACK flood denies service to other users by slowing down or crashing the target using junk data.
The targeted server has to process each ACK packet. It uses so much computing power that it is unable to serve legitimate users.
i. What is an ACK packet?
Data sent over the internet is broken up into smaller segments called packets.
The TCP protocol uses the packet header to tell the recipient the no. of packets present and the order they should arrive.
An ACK packet is any TCP packet that acknowledges receiving a message or series of packets.
Technically, an ACK packet is a TCP packet with the “ACK” flag set in the header:
SYN
————->
SYN/ACK
<————-
ACK
Device1 ————-> Device2
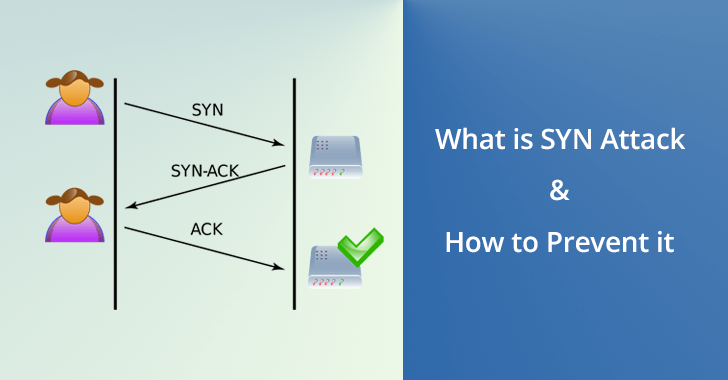
SYN=SYNCHRONIZATION ACK=ACKNOWLEDGEMENTACK packets are part of the TCP handshake, a series of three steps that start a conversation between any two connected devices on the Internet.
a. SYN
b. SYN-ACK
c. ACK
The three-way handshake starts by sending an SYN packet. The device at the other end of the connection replies with an SYN-ACK packet. Finally, the user’s laptop sends an ACK packet.
However, this is not the only time ACK packets are used. The TCP protocol requires that connected devices acknowledge they receive all packets in order.
Since an ACK packet is any TCP packet with the ACK flag, it can be part of a different message the source sends to the server. If we fill out a form and submit data to the server, the source can make one of those packets the ACK packet for the image.
ii. How does an ACK flood attack work?
ACK flood attacks target devices that need to process every packet that they receive. Mostly firewalls and servers are targets for an ACK flood.
They are layer 4 DDoS attacks.
Legitimate and illegitimate ACK packets look essentially the same. Hence, it is difficult to stop them without using a content delivery network (CDN).
Although similar, packets in an ACK DDoS attack do not contain the main part of a data packet. In order to appear legitimate, they only have to include the ACK flag in the TCP header.
iii. How does an SYN-ACK flood attack work?
In an SYN-ACK DDoS attack, the attacker floods the target with SYN-ACK packets. They are not part of a three-way handshake. The only purpose is to disrupt the target’s normal operations.
It is also possible for an attacker to use SYN packets in an SYN flood DDoS attack.
iv. How does CDN stop ACK flood DDoS attacks?
The CDN proxies all traffic to and from a customer's origin server. It does not pass along any ACK packets that are not associated with an open TCP connection.
This ensures that the malicious ACK traffic does not reach the origin server.
[Couldn't fix ACK flood DDoS attack? We'd be happy to assist. ]
Conclusion
This article will guide you on methods to prevent ACK flood #DDoS #attack. An ACK flood DDoS attack occurs when an attacker attempts to overload a server with TCP ACK packets.
Client requests connection by sending #SYN (synchronize) message to the server. Server acknowledges by sending SYN-ACK (synchronize-acknowledge) message back to the client. Client responds with an #ACK (acknowledge) message, and the connection is established.
When computers communicate via TCP, received packets are acknowledged by sending back a packet with an ACK bit set.
The TCP protocol allows these acknowledgements to be included with data that is sent in the opposite direction.
Some protocols send a single acknowledgement per packet of information.
To stop a SYN #DDoS attack:
1. Filtering.
2. Increasing Backlog.
3. TCP half-open: The term half-open alludes to TCP associations whose state is out of synchronization between the two potentially because of an accident on one side.
4. Firewalls and Proxies.
5. Reducing SYN-RECEIVED Timer.
6. SYN Cache.
7. Recycling the Oldest Half-Open TCP.
This article will guide you on methods to prevent ACK flood #DDoS #attack. An ACK flood DDoS attack occurs when an attacker attempts to overload a server with TCP ACK packets.
Client requests connection by sending #SYN (synchronize) message to the server. Server acknowledges by sending SYN-ACK (synchronize-acknowledge) message back to the client. Client responds with an #ACK (acknowledge) message, and the connection is established.
When computers communicate via TCP, received packets are acknowledged by sending back a packet with an ACK bit set.
The TCP protocol allows these acknowledgements to be included with data that is sent in the opposite direction.
Some protocols send a single acknowledgement per packet of information.
To stop a SYN #DDoS attack:
1. Filtering.
2. Increasing Backlog.
3. TCP half-open: The term half-open alludes to TCP associations whose state is out of synchronization between the two potentially because of an accident on one side.
4. Firewalls and Proxies.
5. Reducing SYN-RECEIVED Timer.
6. SYN Cache.
7. Recycling the Oldest Half-Open TCP.