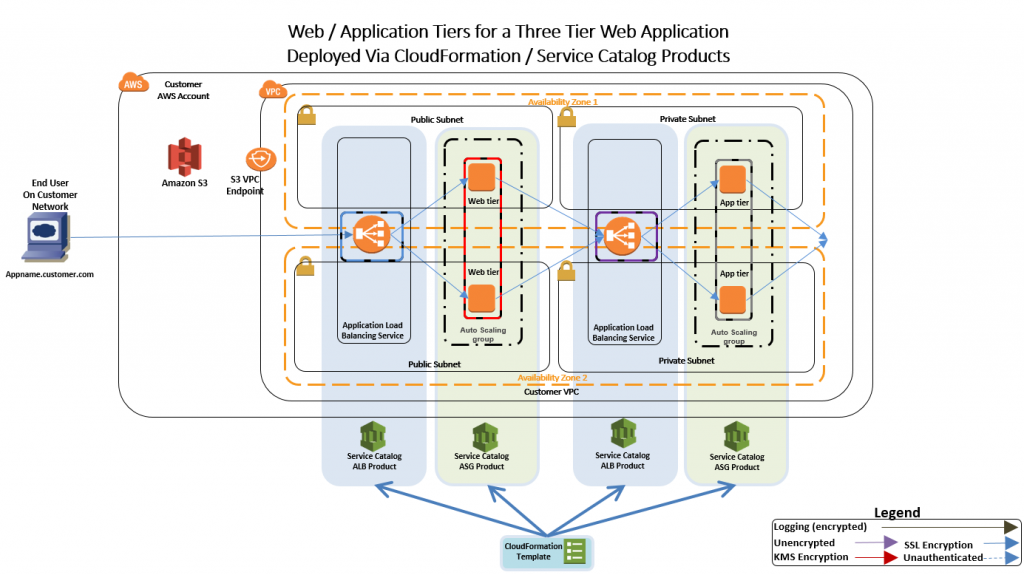
Are you trying to create and configure an AWS load balancer?
This guide is for you.
Elastic Load Balancing automatically distributes incoming application traffic across multiple targets, such as Amazon EC2 instances, containers, IP addresses, Lambda functions, and virtual appliances.
A load balancer serves as the single point of contact for clients. The load balancer distributes incoming traffic across multiple targets, such as Amazon EC2 instances.
A listener checks for connection requests from clients, using the protocol and port that you configure, and forwards requests to a target group.
Here at Ibmi Media, as part of our Server Management Services, we regularly help our Customers to perform AWS related queries.
In this context, we shall look into how to create an Application Load balancer and its dependencies using CloudFormation.
How to create and Configure AWS Application Load Balancer with CloudFormation ?
To do this, follow the steps given below.
Step 1: Create CloudFormation Template for creating AWS Load Balancer
i. First, we use the below code for the CloudFormation template:
AWSTemplateFormatVersion: “2010-09-09”
Description: “Create ALB, ALB security group, target groups, listeners and listener rules”
Parameters:
VPC:
Type: String
Description: The vpc to launch the service
Default: vpc-ID
PublicSubnet1:
Type: String
Description: The subnet where to launch the service
Default: subnet-ID
PublicSubnet2:
Type: String
Description: the subnet where to Launch the service
Default: subnet-ID
Resources:
ALBSecurityGroup:
Type: “AWS::EC2::SecurityGroup”
Properties:
GroupDescription: “security group for ALB”
GroupName: “test-ALB-SG”
Tags:
–
Key: “Project”
Value: “test-blog”
–
Key: “createdBy”
Value: “Ibmi Media”
–
Key: “Environment”
Value: “test”
–
Key: “Name”
Value: “test-ALB-SG”
VpcId: !Ref VPC
SecurityGroupIngress:
–
CidrIp: “0.0.0.0/0”
FromPort: 80
IpProtocol: “tcp”
ToPort: 80
–
CidrIp: “0.0.0.0/0”
FromPort: 443
IpProtocol: “tcp”
ToPort: 443
ApplicationLoadBalancer:
Type: “AWS::ElasticLoadBalancingV2::LoadBalancer”
Properties:
Name: “test-Application-Load-Balancer”
Scheme: “internet-facing”
Type: “application”
Subnets:
– !Ref PublicSubnet1
– !Ref PublicSubnet2
SecurityGroups:
– !Ref ALBSecurityGroup
IpAddressType: “ipv4”
LoadBalancerAttributes:
–
Key: “access_logs.s3.enabled”
Value: “false”
–
Key: “idle_timeout.timeout_seconds”
Value: “60”
–
Key: “deletion_protection.enabled”
Value: “false”
–
Key: “routing.http2.enabled”
Value: “true”
–
Key: “routing.http.drop_invalid_header_fields.enabled”
Value: “false”
HTTPSListener:
Type: “AWS::ElasticLoadBalancingV2::Listener”
Properties:
LoadBalancerArn: !Ref ApplicationLoadBalancer
Port: 443
Protocol: “HTTPS”
SslPolicy: “ELBSecurityPolicy-2016-08”
Certificates:
–
CertificateArn: arn:aws:acm:eu-central-1:**************:certificate/*********************
DefaultActions:
–
Order: 1
TargetGroupArn: !Ref Test1TargetGroup
Type: “forward”
HTTPListener:
Type: “AWS::ElasticLoadBalancingV2::Listener”
Properties:
LoadBalancerArn: !Ref ApplicationLoadBalancer
Port: 80
Protocol: “HTTP”
DefaultActions:
–
Order: 1
RedirectConfig:
Protocol: “HTTPS”
Port: “443”
Host: “#{host}”
Path: “/#{path}”
Query: “#{query}”
StatusCode: “HTTP_301”
Type: “redirect”
Test1TargetGroup:
Type: “AWS::ElasticLoadBalancingV2::TargetGroup”
Properties:
HealthCheckIntervalSeconds: 30
HealthCheckPath: “/”
Port: 80
Protocol: “HTTP”
HealthCheckPort: “traffic-port”
HealthCheckProtocol: “HTTP”
HealthCheckTimeoutSeconds: 5
UnhealthyThresholdCount: 2
TargetType: “instance”
Matcher:
HttpCode: “200”
HealthyThresholdCount: 5
VpcId: !Ref VPC
Name: “target-group-1”
HealthCheckEnabled: true
TargetGroupAttributes:
–
Key: “stickiness.enabled”
Value: “false”
–
Key: “deregistration_delay.timeout_seconds”
Value: “300”
–
Key: “stickiness.type”
Value: “lb_cookie”
–
Key: “stickiness.lb_cookie.duration_seconds”
Value: “86400”
–
Key: “slow_start.duration_seconds”
Value: “0”
–
Key: “load_balancing.algorithm.type”
Value: “round_robin”
Test2TargetGroup:
Type: “AWS::ElasticLoadBalancingV2::TargetGroup”
Properties:
HealthCheckIntervalSeconds: 30
HealthCheckPath: “/”
Port: 80
Protocol: “HTTP”
HealthCheckPort: “traffic-port”
HealthCheckProtocol: “HTTP”
HealthCheckTimeoutSeconds: 5
UnhealthyThresholdCount: 2
TargetType: “instance”
Matcher:
HttpCode: “200”
HealthyThresholdCount: 5
VpcId: !Ref VPC
Name: “target-group-2”
HealthCheckEnabled: true
TargetGroupAttributes:
–
Key: “stickiness.enabled”
Value: “false”
–
Key: “deregistration_delay.timeout_seconds”
Value: “300”
–
Key: “stickiness.type”
Value: “lb_cookie”
–
Key: “stickiness.lb_cookie.duration_seconds”
Value: “86400”
–
Key: “slow_start.duration_seconds”
Value: “0”
–
Key: “load_balancing.algorithm.type”
Value: “round_robin”
TestListenerRule1:
Type: “AWS::ElasticLoadBalancingV2::ListenerRule”
Properties:
Priority: “1”
ListenerArn: !Ref HTTPSListener
Conditions:
–
Field: “host-header”
Values:
– “test1.blog.avrcr.com”
Actions:
–
Type: “forward”
TargetGroupArn: !Ref Test1TargetGroup
Order: 1
ForwardConfig:
TargetGroups:
–
TargetGroupArn: !Ref Test1TargetGroup
Weight: 1
TargetGroupStickinessConfig:
Enabled: false
TestListenerRule2:
Type: “AWS::ElasticLoadBalancingV2::ListenerRule”
Properties:
Priority: “2”
ListenerArn: !Ref HTTPSListener
Conditions:
–
Field: “host-header”
Values:
– “test2.blog.com”
Actions:
–
Type: “forward”
TargetGroupArn: !Ref Test2TargetGroup
Order: 1
ForwardConfig:
TargetGroups:
–
TargetGroupArn: !Ref Test2TargetGroup
Weight: 1
TargetGroupStickinessConfig:
Enabled: false
Outputs:
ALB:
Description: The created loadbalancer
Value: !Ref ApplicationLoadBalancer
TargetGroup1:
Description: The created TargetGroup 1
Value: !Ref Test1TargetGroup
TargetGroup2:
Description: The created TargetGroup 2
Value: !Ref Test2TargetGroup
LoadBalancerSecurityGroup:
Description: the securty group for the ALB
Value: !Ref ALBSecurityGroupii. Here is the explanation for the CloudFormation Template.
The template comprises of 3 sections: Parameters, Resources and Outputs.
Parameters section
The user inputs their dynamic variables in the parameters section. Also, the user can customize the template by inputting their VPC and Subnets IDs.
In our case, the load balancer is internet-facing hence we need to have it created on public subnets.
Resources Section
In this section, the user can define the AWS resources they create.
1. Here, on our template, first, we create the load balancer security group. It allows inbound traffic from port 80 and 443.
2. Next, the template creates a load balancer. Here, the user can customize the name of the load balancer, the scheme, or whether it will be internal or internet-facing.
3. The template creates the two listeners for the load balancer as we have opened port 80 and 443.
4. Next, the template creates two target groups.
5. Finally, the template creates listener rules.
Outputs Section
This section outputs the names of the resources we created.
Step 2: Create CodePipeline to Deploy Template
1. We use the below code cloudformation template to create the CodePipeline role to deploy the template to CloudFormation:
AWSTemplateFormatVersion: “2010-09-09”
Description: “Template to create centos ec2 instance and install ssm on it”
Resources:
IAMInstanceRole:
Type: ‘AWS::IAM::Role’
Properties:
Description: The SSM Instance Profile
RoleName: codepipeline-test
AssumeRolePolicyDocument:
Version: 2012-10-17
Statement:
– Effect: Allow
Principal:
Service:
– cloudformation.amazonaws.com
Action:
– ‘sts:AssumeRole’
ManagedPolicyArns:
– arn:aws:iam::aws:policy/AWSCloudFormationFullAccess
– arn:aws:iam::aws:policy/CloudWatchFullAccess
– arn:aws:iam::aws:policy/AmazonEC2FullAccess
Tags:
–
Key: “Project”
Value: “test-blog”
–
Key: “Environment”
Value: “test”
–
Key: “createdBy”
Value: “Ibmi Media”
–
Key: “Name”
Value: “codepipeline-test”
IAMInstanceProfile:
Type: AWS::IAM::InstanceProfile
Properties:
InstanceProfileName: codepipeline-test
Roles:
– !Ref IAMInstanceRole
Outputs:
Profile:
Description: The created Instance Profile
Value: !Ref IAMInstanceProfile
Role:
Description: The created role
Value: !Ref IAMInstanceRole2. Next, we go to the CodeCommit console. Here, we create a code commit repository.
Then we commit the alb template to the repository.
3. On the CodePipeline console, we select create pipeline.
4. After that, we choose pipeline settings. For service role, we opt to create a new service role.
5. Also, under Advanced Settings, we choose the S3 bucket that we will use to store the artifacts. For the encryption key, we choose the default AWS key. Then we click next.
6. On the add source stage screen, we choose code commit as the source provider.
7. We then enter the details of the CodeCommit repository name and the branch. Also, for change detection we leave the setting to Amazon CloudWatch Events. This enables CloudWatch to detect changes made on the code and auto-start the pipeline to update those changes. When done we click next.
8. On the add build stage screen, we click skip build stage.
9. Finally, on the add deploy stage screen, we select CloudFormation as the deployment option.
10. We then fill in the details for the CloudFormation deployment.
11. The next stage allows the user to review all the configurations done. If all configurations are correct, we click on create pipeline.
12. Finally, now we have created the first pipeline to deploy a CloudFormation template.
[Still, not able to create AWS load balancer? – We are here to help you. ]
Conclusion
This article will guide you on how to create an Application Load balancer and its dependencies using CloudFormation.
Load balancing is defined as the methodical and efficient distribution of network or application traffic across multiple servers in a server farm.
Each load balancer sits between client devices and backend servers, receiving and then distributing incoming requests to any available server capable of fulfilling them.
Software load balancers is that hardware load balancers require proprietary, rack-and-stack hardware appliances, while software load balancers are simply installed on standard x86 servers or virtual machines.
Another critical difference between hardware and software load balancers lies in the ability to scale.
Elastic Load Balancing supports the following types of load balancers:
1. Application Load Balancers, Network Load Balancers, and Classic Load Balancers.
2. Amazon ECS services can use either type of load balancer.
3. Application Load Balancers are used to route HTTP/HTTPS (or Layer 7) traffic.
This article will guide you on how to create an Application Load balancer and its dependencies using CloudFormation.
Load balancing is defined as the methodical and efficient distribution of network or application traffic across multiple servers in a server farm.
Each load balancer sits between client devices and backend servers, receiving and then distributing incoming requests to any available server capable of fulfilling them.
Software load balancers is that hardware load balancers require proprietary, rack-and-stack hardware appliances, while software load balancers are simply installed on standard x86 servers or virtual machines.
Another critical difference between hardware and software load balancers lies in the ability to scale.
Elastic Load Balancing supports the following types of load balancers:
1. Application Load Balancers, Network Load Balancers, and Classic Load Balancers.
2. Amazon ECS services can use either type of load balancer.
3. Application Load Balancers are used to route HTTP/HTTPS (or Layer 7) traffic.