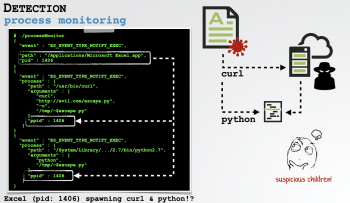
Malicious TMP files and processes
This article covers method to resolve malicious tmp processes. Most malware installers delete itself and these TMP files after successful installation.
The use of TMP files for atomicity is an advantage attackers currently enjoy.
They could have done this operation in any folder of the system, but they choose to use the standard Windows Temp folder.
The first thing a malware installer (first stage of infection) does when executed on a target system - be it a dropper or downloader - is to install a copy of the malware and its components into their corresponding location in the system.
Install vnStat in Linux to monitor network traffic
This article covers how to install and configure vnStat in Linux. Also, you will see how to resolve some common errors relating to it.
#vnStat (view network statistics) is a network utility for the #Linux operating system.
It uses a command line interface. vnStat command is a console-based network #traffic #monitor.
It keeps a log of hourly, daily and monthly network traffic for the selected interface(s) but is not a packet sniffer.
Features of vnStat:
1. quick and simple to install and get running
2. gathered statistics persists through system reboots
3. can monitor multiple interfaces at the same time
4. data retention duration is fully user configurable on the fly
5. months can be configured to follow billing period
6. light, minimal resource usage
7. same low cpu usage regardless of traffic
8. can be used without root permissions
9. online color configuration editor
Automate WordPress Deployments using Buddy
This article covers how to automate #WordPress #deployments using Buddy. Buddy has become the foundation of every WordPress project you need to create. With Buddy you can run really complicated deployments with just one click. It also helps me to update plugins and monitor the uptime.
You can automate anything including sales, marketing, administrative tasks, learning and any other kind of processes you want letting you save time and get focused on your most important work.
BackupBuddy is one of the most reliable WordPress backup plugins that can help you back up your whole WordPress website installation.
Features of #Buddy:
1. Composer - Automatically install dependencies on server on every commit.
2. Zero-downtime deployments - Ensure 100% uptime of your websites with preconfigured atomic deployment templates.
3. Test-ready - Easily introduce unit and browser tests to improve the quality of your websites.
4. Docker support - Standarize your development environment and fast-track release times with Docker.
5. Real-time monitoring - Monitor websites for performance, SEO, and accessibility. Receive warnings when things go wrong.
6. WP-CLI - Run WordPress scripts to perform backups, update WP core, and migrate DB's.
Configure AWS load balancer with Cloudformation
This article will guide you on how to create an Application Load balancer and its dependencies using CloudFormation.
Load balancing is defined as the methodical and efficient distribution of network or application traffic across multiple servers in a server farm.
Each load balancer sits between client devices and backend servers, receiving and then distributing incoming requests to any available server capable of fulfilling them.
Software load balancers is that hardware load balancers require proprietary, rack-and-stack hardware appliances, while software load balancers are simply installed on standard x86 servers or virtual machines.
Another critical difference between hardware and software load balancers lies in the ability to scale.
Elastic Load Balancing supports the following types of load balancers:
1. Application Load Balancers, Network Load Balancers, and Classic Load Balancers.
2. Amazon ECS services can use either type of load balancer.
3. Application Load Balancers are used to route HTTP/HTTPS (or Layer 7) traffic.
AWS error establishing a database connection
AWS error establishing a database connection happens as a result of different reasons that include corrupt MySQL, webserver down, bot hitting the server load, and so on.
AWS Error establishing a database connection means that the username and password information in your wp-config.php file is incorrect or we can't contact the database server.
This could mean your host's database server is down.
Are you sure you have the correct username and password?
Are you sure that you have typed the correct hostname?
Are you sure that the database server is running?
The inability to connect to an Amazon RDS DB instance can have a number of root causes. The wrong DNS name or endpoint was used to connect to the DB instance.
The Multi-AZ DB instance failed over, and the secondary DB instance uses a subnet or route table that doesn't allow inbound connections.
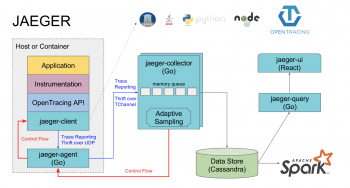
Distributed Tracing with Jaeger on Kubernetes
This article will guide you on implementing Distributed Tracing with Jaeger on Kubernetes where you will be able to find the cause of our irregular response time.
The Jaeger agent is a network daemon that listens for spans sent over UDP, which it batches and sends to the collector. It is designed to be deployed to all hosts as an infrastructure component.
The agent abstracts the routing and discovery of the collectors away from the client.
1. Application tracing allows you to log information when a program is executing.
2. Tracing is used to help you identify issues with your application (performance of the app or simply debugging an issue) instead of going through stack traces.
3. At a high level, log monitoring helps to speed up the process of identifying specific exceptions, when these exceptions occur and the frequency at which they occur. 4. Additionally, it provides developers and support personnel with a greater level of visibility into the systems and applications being monitored.
5. Insufficient logging and monitoring vulnerability occur when the security-critical event is not logged off properly, and the system is not monitored.
6. Lack of such functionalities can make malicious activities harder to detect and in turn affects the incident handling process.