To ensure a high level of security for user accounts in the Active Directory domain, an administrator must configure and implement a domain password policy. The password policy should provide sufficient complexity, password length, and the frequency of changing of user and service account passwords. Thus, you can make it hard for an attacker to brute-force or capture user passwords when send over a network.
We configure Domain Password Policy in the Active Directory to ensure a high level of security for user accounts.
With sufficient complexity, password length, and the frequency of changing user and service account passwords, it will be hard for an attacker to brute-force or capture user passwords.
Here at Ibmi Media, as part of our Server Management Services, we regularly help our Customers to perform Active Directory queries.
In this context, we shall look into how to configure Domain Password Policy in the Active Directory.
Password Policy in the Default Domain Policy
By default, we use the Group Policy (GPO) settings to set common requirements for user passwords in the AD domain.
This policy links to the root of the domain and must apply to a domain controller with the PDC emulator role.
To configure the AD account password policy, our Support Experts suggest the following steps:
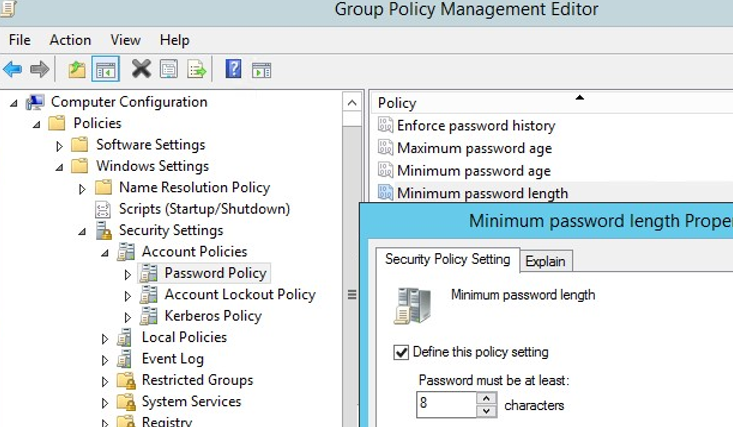
1. Initially, open the Group Policy Management console (gpmc.msc)
2. Expand the domain and find the GPO named Default Domain Policy. Right-click it and select Edit
3. Password policies are in: Computer configuration-> Policies-> Windows Settings->Security Settings -> Account Policies -> Password Policy
4. Double-click a policy setting to edit it. To enable a specific policy setting, check the Define this policy setting and specify the necessary value. Save the changes.
5. This will set a new password policy to all domain computers in the background, during computer boot or we can apply the policy immediately by running the gpupdate /force command.
We can change the password policy settings from the GPO Management Console or by using:
Set-ADDefaultDomainPasswordPolicy -Identity ibmimedia.com -MinPasswordLength 10 -LockoutThreshold 3Basic Password Policy Settings on Windows
There are six password settings in GPO:
1. Enforce password history
Here, we can determine the number of old passwords in AD, thus preventing a user from using an old password.
However, the domain admin or user who has password reset permissions can manually set the old password for the account.
2. Maximum password age
Here, we can set the password expiration in days. Once it expires, Windows will ask us to change the password.
To find when a specific user’s password expires, we run:
Get-ADUser -Identity c.bob -Properties msDS-UserPasswordExpiryTimeComputed | select-object @{Name=”ExpirationDate”;Expression= {[datetime]::FromFileTime($_.”msDS-UserPasswordExpiryTimeComputed”)}}3. Minimum password length
It is recommended to have passwords that contain at least 8 symbols.
4. Minimum password age
This sets how often we can change passwords. This will not allow the user to change the password too often to get back to an old password by removing them from the Password History once the password changes several times in a row.
As a precaution, it is worth setting 1 day here in order for users to change a password themselves if it compromises.
5. Password must meet complexity requirements
Once we enable the policy, a user cannot use the account name in a password, also 3 types of symbols must be used in the password: numbers (0–9), uppercase letters, lowercase letters, and special characters.
In addition, to prevent weak passwords, we recommend regularly audit user passwords in the AD domain.
6. Store passwords using reversible encryption
User passwords encrypt in the AD database, but in some cases, we have to grant access to user passwords to some apps. If we do so, passwords are less protected. It is not secure.
If a user tries to change a password that does not match the password policy in the domain, the error message will appear:
Unable to update the password. The value provided for the new password does not meet the length, complexity, or history requirements of the domain.
Additionally, we should configure the following password settings in the GPO section Account Lockout Password:
1. Account Lockout Threshold: the number of failed sign-in attempts that can be made by the user prior to the lockout of his account.
2. Account Lockout Duration: how long an account will lock if the user enters the wrong password several times.
3. Reset account lockout counter after – the number of minutes after which the Account Lockout Threshold counter will be reset.
If the specific domain account locks out too often, we can identify the source of account lockouts using this method.
The default settings of password policies in the AD domain are:
Policy Default value
Enforce password history 24 passwords
Maximum password age 42 days
Minimum password age 1 day
Minimum password length 7
Password must meet complexity requirements Enabled
Store passwords using reversible encryption Disabled
Account lockout duration Not set
Account lockout threshold 0
Reset account lockout counter after Not setGenerally, Microsoft recommends using the following password policy settings:
i. Enforce Password History: 24
ii. Maximum password age: not set
iii. Minimum password age: not set
iv. Minimum password length: 14
v. Password must meet complexity: Enabled
vi. Store passwords using reversible encryption: Disabled
How to Check the Current Password Policy in AD Domain ?
We can see the current password policy settings in the Default Domain Policy in the gpmc.msc console (on the Settings tab).
We can also display password policy information using the command:
Get-ADDefaultDomainPasswordPolicy
ComplexityEnabled: True
DistinguishedName: DC=woshub,DC=com
LockoutDuration: 00:20:00
LockoutObservationWindow: 00:30:00
LockoutThreshold: 0
MaxPasswordAge: 60.00:00:00
MinPasswordAge: 1.00:00:00
MinPasswordLength: 8
objectClas : {domainDNS}
PasswordHistoryCount: 24
ReversibleEncryptionEnabled: FalseIn addition, we can check the current AD password policy settings on any domain computer using the gpresult command.
Multiple Password Policies in an Active Directory Domain
The domain controller, the owner of the PDC Emulator FSMO role, manages the domain password policy. Domain administrator rights are to edit the Default Domain Policy settings.
Initially, we have only one password policy in the domain, which applies to the domain root and affects all users without exception.
Domain password policy only affects user AD objects.
Prior to Active Directory in Windows Server 2008, only one password policy could be configured per domain.
However, in newer versions of AD, we can create multiple password policies for different users or groups using the Fine-Grained Password Policies (FGPP).
For example, we can create a PSO with increased password length or complexity for domain admin accounts or make passwords of some accounts more simple or even disable them completely.
In a workgroup environment, we have to configure password policies on each computer with the local GPO editor – gpedit.msc.
[Need urgent help with Active Directory configuration? We are here for you. ]
Conclusion
This article covers an effective method to configure Domain Password Policy in the Active Directory which ensures a high level of security for user accounts.
Group policy with password policy should be assigned to domain level, not OU, you can have multiple GPO's with password policies in domain level however only one policy will be applied to all users in their priority.
Basic Password Policy Settings on Windows:
Let's consider all available Windows password settings.
There are six password settings in GPO:
1. Enforce password history – determines the number of old passwords stored in AD, thus preventing a user from using an old password.
However, the domain admin or user who has been delegated password reset permissions in AD can manually set the old password for the account;
2. Maximum password age – sets the password expiration in days. After the password expires, Windows will ask the user to change the password. Ensures the regularity of password changes by users;
You can find out when a specific user’s password expires using the PowerShell:
Get-ADUser -Identity j.werder -Properties msDS-UserPasswordExpiryTimeComputed | select-object @{Name="ExpirationDate";Expression= {[datetime]::FromFileTime($_."msDS-UserPasswordExpiryTimeComputed") }}.
3. Minimum password length – it is recommended that passwords should contain at least 8 symbols (if you specify 0 here, the password is not required);
4. Minimum password age – sets how often users can change their passwords. This setting won’t allow the user to change the password too often to get back to an old password they like by removing them from the Password History after the password has been changed several times in a row. As a rule, it is worth to set 1 day here in order users can change a password themselves if it gets compromised (otherwise an administrator will have to change it);
5. Password must meet complexity requirements – if the policy is enabled, a user cannot use the account name in a password (not more than 2 symbols of a username or Firstname in a row), also 3 types of symbols must be used in the password: numbers (0–9), uppercase letters, lowercase letters and special characters ($, #, %, etc.). Also, to prevent using weak passwords (from the password dictionary), it is recommended to regularly audit user passwords in the AD domain;
6. Store passwords using reversible encryption – user passwords are stored encrypted in the AD database, but in some cases you have to grant access to user passwords to some apps. If this policy setting is enabled, passwords are less protected (almost plain text). It is not secure (an attacker can get access to the password database if the DC is compromised; an read-only domain controllers (RODC) can be used as one of the protection measures).
This article covers an effective method to configure Domain Password Policy in the Active Directory which ensures a high level of security for user accounts.
Group policy with password policy should be assigned to domain level, not OU, you can have multiple GPO's with password policies in domain level however only one policy will be applied to all users in their priority.
Basic Password Policy Settings on Windows:
Let's consider all available Windows password settings.
There are six password settings in GPO:
1. Enforce password history – determines the number of old passwords stored in AD, thus preventing a user from using an old password.
However, the domain admin or user who has been delegated password reset permissions in AD can manually set the old password for the account;
2. Maximum password age – sets the password expiration in days. After the password expires, Windows will ask the user to change the password. Ensures the regularity of password changes by users;
You can find out when a specific user’s password expires using the PowerShell:
Get-ADUser -Identity j.werder -Properties msDS-UserPasswordExpiryTimeComputed | select-object @{Name="ExpirationDate";Expression= {[datetime]::FromFileTime($_."msDS-UserPasswordExpiryTimeComputed") }}.
3. Minimum password length – it is recommended that passwords should contain at least 8 symbols (if you specify 0 here, the password is not required);
4. Minimum password age – sets how often users can change their passwords. This setting won’t allow the user to change the password too often to get back to an old password they like by removing them from the Password History after the password has been changed several times in a row. As a rule, it is worth to set 1 day here in order users can change a password themselves if it gets compromised (otherwise an administrator will have to change it);
5. Password must meet complexity requirements – if the policy is enabled, a user cannot use the account name in a password (not more than 2 symbols of a username or Firstname in a row), also 3 types of symbols must be used in the password: numbers (0–9), uppercase letters, lowercase letters and special characters ($, #, %, etc.). Also, to prevent using weak passwords (from the password dictionary), it is recommended to regularly audit user passwords in the AD domain;
6. Store passwords using reversible encryption – user passwords are stored encrypted in the AD database, but in some cases you have to grant access to user passwords to some apps. If this policy setting is enabled, passwords are less protected (almost plain text). It is not secure (an attacker can get access to the password database if the DC is compromised; an read-only domain controllers (RODC) can be used as one of the protection measures).