Are you trying to figure out how to set up Azure multi-factor authentication?
This tutorial is for you.
Microsoft Azure, commonly referred to as Azure is a cloud computing service created by Microsoft for building, testing, deploying, and managing applications.
Here at Ibmi Media, as part of our Server Management Services, we regularly help our Customers to perform Azure related tasks.
Here, we shall look into how to set up Azure multi-factor authentication.
Steps to set up Azure multi-factor authentication?
Multi-factor authentication refers to the system in which more than one system authenticates the user to access an application. This authentication offers better security for Azure clients.
In this process, first, the user signs in with the username and password in a normal way. The credentials are verified and then if the automated call authentication is activated, the user receives a call and is asked to confirm the sign-in attempt.
Now let us take a look at how our Support Experts configured the Azure Multi-Factor Authentication.
How to create a Multi-Factor Authentication Provider?
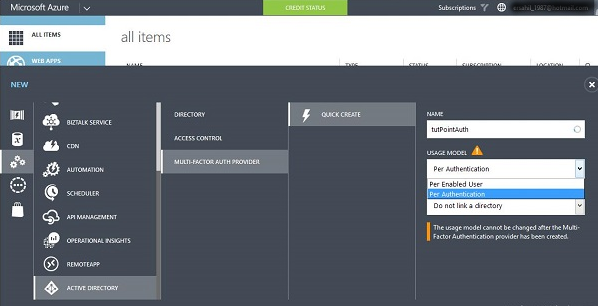
1. In Microsoft Azure, we click on "New" at the left bottom corner >> "App Services >> Active Directory >> Multi Factor Auth Provider >> Quick Create".
2. Next, we enter the name of the provider.
3. Then we select the Usage model. Here, we are considering ‘Per Authentication’
Note: It is not possible to change the usage model once a multi-authentication provider is created. So we need to consider the needs before choosing.
4. Now we get an option about if we wish we can link the existing directory or not. Here, we are linking an existing directory name "ibmimedia" that we previously created for a multi-factor provider.
5. After we click on "Create", it will list in our services list. Then we select the multi-factor provider that we just created.
6. We select "Manage" at the bottom of the screen and we will be taken to a new page.
7. Here, we select "Configure" to choose the authentication.
8. Here, we can set the number of attempts, change the phone number from where the call is made (default number is already there), two-way message timeout (default is 60 seconds), one-time password’s timeout (default is 300 seconds) under general settings. Also, we can provide an email address where we can be notified if a one-time password is bypassed.
9. When we scroll down the page, we see the fraud settings. Under Fraud Setting, we can choose to allow the users to send fraud alerts, block the user if an alert is reported, and also set an e-mail address where alerts are sent.
This activates the multi-factor authentication. The users will be asked to choose one of the three methods (automated message, text message, or mobile app) when they sign in to their account next time. This chosen method will be used to authenticate them each time they sign in to their account.
How to enable the Multi-Factor Authentication for Existing Directory?
In the previous section, we saw how to link the directory to a multi-factor authentication provider while creating it. However, we can also do it for a particular user in the following way.
Start by navigating to the directory by choosing it from the left panel and click "Manage MultiFactor Auth" at the bottom of the screen.
In the next screen, we select the user and enable or disable the multi-factor authentication for the user.
[Need urgent support with Azure queries? – We are available to help you today.]
Conclusion
This article will guide you on the complete process to set up Azure multi-factor authentication.
This article will guide you on the complete process to set up Azure multi-factor authentication.