Having issues configuring Zabbix: Single Sign-On (SSO) Authentication in Active Directory?
This guide will help you.
Single Sign On is used to mean visiting an internal web page carries your Windows login permissions and the web server can act on them.
Here at Ibmi Media, as part of our Server Management Services, we regularly help our Customers to perform related configurations.
In this context, we shall look into how to set up SSO Authentication in Active Directory for Zabbix.
Zabbix: Single Sign-On (SSO) Authentication in Active Directory
Here, will we look into the step-by-step configuration of a transparent SSO (Single Sign-On) authentication for Zabbix in Active Directory using Kerberos.
The end result is that a user is automatically authenticated on the Zabbix frontpage without entering credentials.
To do it, a user must be logged in to Windows under the Active Directory domain account specified in Zabbix. In addition, the user must configure the browser.
To begin, You need to have:
i. Ubuntu Server 18.04 LTS.
ii. Active Directory domain with functional level 2008 (or higher).
iii. Zabbix Server 4.0.11, Apache2 as a web server.
Zabbix LDAP Authentication on Active Directory
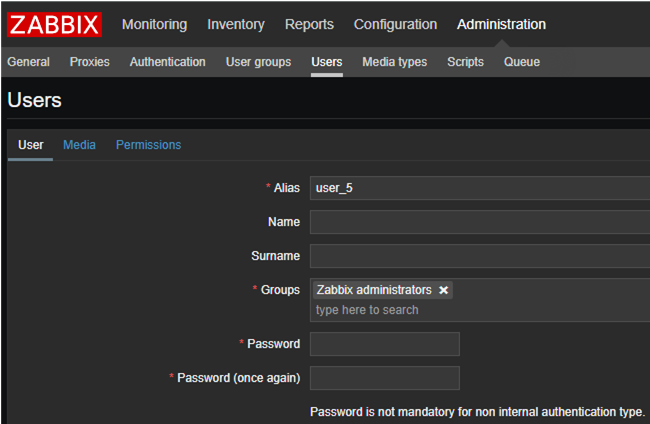
First of all, we have to bind domain users to Zabbix. To do it, it is enough to create a user in Zabbix with the same login as they have in the AD domain.
For example, if the login (sAMAccountName attribute) is user_5, a user in Zabbix must have the same login.
Do it for each user.
Then create a separate user account in Active Directory to bind Zabbix to our domain.
In practice, we can use any domain account, but it is better to create a separate service account. In this case, it will be zabbix_admin.
To create a user in AD, we will use:
New-ADUser -Name “zabbix_admin” -GivenName “zabbix_admin” -Surname “zabbix_admin” -SamAccountName “zabbix_admin” -AccountPassword (Read-Host -AsSecureString “Password:”) -DisplayName “zabbix_admin” -Enabled $trueRun the command and set a user password. Our new user will be under the Users container in the root of the domain.
Let us configure LDAP authentication in Zabbix. In the Zabbix frontend, go to the LDAP settings tab in Administration -> Authentication.
Check Enable LDAP authentication and fill in the following fields:
i. LDAP host: ldap://dc1.domain.local
ii. Port: 389
iii. Base DN: DC=domain, DC=local
iv. Search attribute: sAMAccountName
v. Bind DN: CN=zabbix_admin,OU=Users,DC=domain,DC=local
Before completing the configuration, make sure that the settings are valid by doing a test login. Specify a user name and an AD password.
If the test has been successful, save the settings, and change the authentication type in Zabbix from Internal to LDAP.
Enable HTTP authentication (HTTP Settings -> Enable HTTP authentication):
LDAP authentication is configured. If the LDAP server is unavailable, we will not be able to access Zabbix.
To get back to the internal authentication, we open MySQL, and run the following command:
update zabbix.config set authentication_type=’0′ where configid=’1′;How to Configure a Transparent (Single Sign-On) Authentication in Zabbix?
Initially, specify the FQDN name of the server in /etc/hostname that must match the DNS record in the domain. In this case, it is zabbix.domain.local.
Also, write the FQDN of the server for the local IP address and the IP address of the server in /etc/hosts.
127.0.0.1 localhost zabbix.domain.local10.1.1.10 zabbix.domain.localIn order for Kerberos authentication to work, synchronize time with the domain controller. Install the ntpdate package and bind it to the domain controller.
apt-get install ntp ntpdatentpdate dc.domain.localChrony is to synchronize time in CentOS 8. The ntp and ntpdate packages are not available in the official repositories.
Now we need to generate a keytab file on a domain controller.
Keytab is a file that contains SPN and encrypted keys. Keytab is used for Kerberos-based authentication.
i. Log in on the domain controller and run the command prompt as an administrator. Go to C:\.
ii. Then enter the following:
ktpass -princ HTTP/zabbix.domain.local@DOMAIN.LOCAL -mapuser zabbix_admin -pass STRONGPASS -crypto ALL -ptype KRB5_NT_PRINCIPAL -out zabbix.keytab -setupn –setpassCopy C:\zabbix.keytab file to /etc/apache2/ directory on Zabbix server.iii. Install Kerberos packages and a module for apache2:
#apt install krb5-user libapache2-mod-auth-kerbiv. Then, configure krb5-user. Edit /etc/krb5.cnf:
[logging]default = FILE:/var/log/krb5libs.logkdc = FILE:/var/log/krb5kdc.logadmin_server = FILE:/var/log/kadmind.log[libdefaults]default_realm = DOMAIN.LOCALdefault_keytab_name = /etc/apache2/zabbix.keytabdns_lookup_kdc = falsedns_lookup_realm = falseforwardable = trueticket_lifetime = 24h[realms]DOMAIN.LOCAL = {kdc = dc.domain.localdefault_domain = DOMAIN.LOCALadmin_server = dc.domain.local}[domain_realm].domain.local = DOMAIN.LOCALdomain.local = DOMAIN.LOCALv. Specify the domain. In some places, the domain name is written in upper case, follow this rule.
vi. On the other hand look at the line with keytab file path “default_keytab_name = /etc/apache2/zabbix.keytab”. Then make sure that the file is available there.
vii. Grant read permissions on www-data and run:
chown www-data:www-data /etc/apache2/zabbix.keytabviii. Make sure that Kerberos authentication is working in Linux:
kinit -kV -p HTTP/zabbix.domain.local –t /etc/apache2/zabbix.keytabWe may see this error:
kinit: Client ‘HTTP/zabbix.domain.local@DOMAIN.LOCAL’ not found in Kerberos database while getting initial credentialsIn this case, try to authenticate using the credentials of another user:
kinit -pV LOGINIf the authentication is successful, the problem is with the keytab file. Check if the command to create a keytab file is correct.
Then we make sure that an SPN record for the Zabbix service account exists in AD.
Enter the following command on the domain controller:
setspn -l zabbix_adminWe will see a message like this. It must be in HTTP/zabbix.domain.local format. If there is no record, add it.
setspn -a HTTP/zabbix.domain.local zabbix_adminMake sure that the user login name changed to HTTP/zabbix.domain.local.
If it has not, change it manually.
Then edit the apache2 configuration file – /etc/apache2/sites-available/000-default.conf.
Later, add the following under the ServerName zabbix.domain.local line:
<Location />AuthType KerberosAuthName “Kerberos authenticated”KrbAuthRealms DOMAIN.LOCAL#KrbServiceName HTTP/zabbix.domain.localKrbServiceName AnyKrb5Keytab /etc/apache2/zabbix.keytabKrbMethodNegotiate OnKrbSaveCredentials onKrbLocalUserMapping onRequire valid-user</Location>If KrbServiceName does not match the name specified in the keytab file, an error occurs. So we can set Any value while testing. After making sure that the system is working, specify the valid service name.
We can check it using:
klist -le /etc/apache2/zabbix.keytab[Set up SSO Authentication quick! We are here for you!]
How to Configure Browsers for Kerberos Authentication?
For Internet Explorer to use Kerberos authentication on Zabbix, we will have to add its URL to Local Intranet sites.
Google Chrome uses Internet Explorer settings, so we do not need to configure it separately.
i. Open Options -> Security in the IE.
ii. Click Sites in the Local intranet, check the options shown in the screenshot below, and click Advanced:
iii. Later, enter the Zabbix server URL.
iv. Then, go to the Advanced tab and check Enable Integrated Windows Authentication.
v. Also, we can also put Zabbix URL to the Local Intranet zone using the Group Policies (Computer Configuration -> Administrative Templates -> Windows Components -> Internet Explorer -> Internet Control Panel -> Security Page -> Site to Zone Assignment List. Use zone code 1 for intranet sites).
vi. Add the URL of the Zabbix server to the following parameters of about:config for Mozilla Firefox:
network.automatic-ntlm-auth.trusted-urisnetwork.negotiate-auth.delegation-urisnetwork.negotiate-auth.trusted-urisThe configuration is over. If we try to access the Zabbix server URL, we will be authenticated automatically and will not be prompted to enter the password.
[Couldn't configure Linux Packages? Contact us now]
Kerberos Authentication Debugging & Troubleshooting in Apache
If we have any issues, enable debug mode in apache2:
Enter the following before the closing </VirtualHost> tag in /etc/apache2/sites-available/000-defaults.conf:
LogLevel trace8Then we restart apache and check the Kerberos module error in the error.log file.
To make it more convenient, we use the command to filter the entries by the IP address:
tail -f /var/log/apache2/error.log | grep ‘Our IP address’Similarly, to work with and diagnose Kerberos, we can use kinit and klist commands.
kinit is a tool to get and cache Kerberos tickets, for example:
kinit –V -k -t /etc/apache2/zabbix.keytab –p HTTP/zabbix.domain.local@DOMAIN.LOCALIf we have generated our keytab file correctly, the command will run. As a result, we will get a message that the authentication has been successful.
Using klist, we can view cached Kerberos tickets:
klist -a
[Finding it hard to set Firewall in Ubuntu? We'd be happy to assist. ]
Conclusion
This article will guide you on how to set #Zabbix : Single Sign-On (#SSO) Authentication in #Active Directory which helps users authenticate the Zabbix frontpage without entering credentials.
Users and resources are added to the directory service for central management and ADDS works with authentication protocols like #NTLM and #Kerberos. Thus, users that belong to ADDS can authenticate from their #machines and get access to others #systems that integrate with ADDS. This is a form of Single Sign-on.
This article will guide you on how to set #Zabbix : Single Sign-On (#SSO) Authentication in #Active Directory which helps users authenticate the Zabbix frontpage without entering credentials.
Users and resources are added to the directory service for central management and ADDS works with authentication protocols like #NTLM and #Kerberos. Thus, users that belong to ADDS can authenticate from their #machines and get access to others #systems that integrate with ADDS. This is a form of Single Sign-on.