Are you trying to to mitigate DNS amplification attack?
This guide is for you.
We know that DDoS tries to deny the important services that run on the server by sending enormous traffic to the destination server so that the server can’t handle them.
DNS amplification is a Distributed Denial of Service (DDoS) attack in which the attacker exploits vulnerabilities in domain name system (DNS) servers to turn initially small queries into much larger payloads, which are used to bring down the victim's servers. So it is important to protect servers from DDoS to avoid server downtime.
In a DNS amplification attack, malicious actors take advantage of the normal operation of the Domain Name System (DNS)—the “address book” of the Internet—using it as a weapon against a targeted victim's website.
Here at Ibmi Media, as part of our Server Management Services, we regularly help our Customers to prevent DDoS attacks.
In this context, we shall look into how our Support Experts mitigate DNS Amplification Attack for our customers.
Nature of DNS amplification attack ?
Before going into the steps to mitigate we see how this DNS amplification attack works.
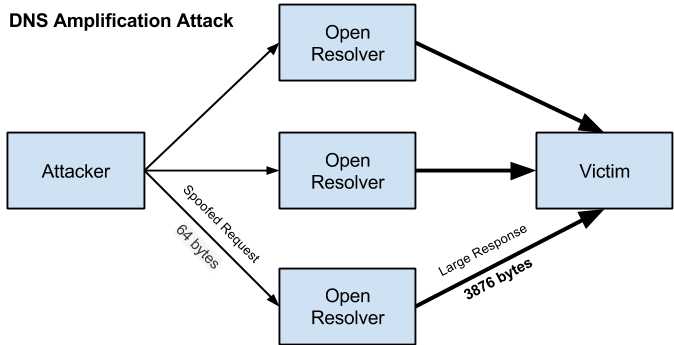
A DNS amplification can be broken down into four steps:
1. Firstly, the attacker uses a compromised endpoint to send UDP packets with spoofed IP addresses to a DNS recursor. This spoofed address on the packets points to the real IP address of the victim.
2. Each one of the UDP packets makes a request to a DNS resolver, often passing an argument such as “ANY” in order to receive the largest response possible.
3. After receiving the requests, the DNS resolver, which is trying to be helpful by responding, sends a large response to the spoofed IP address.
4. The IP address of the target receives the response and the surrounding network infrastructure faces high traffic, resulting in a denial-of-service.
Ways to mitigate DNS amplification attack?
Now let's see the steps which our Support Experts follow to mitigate DNS amplification attack.
Most of the time the Internet Service Provider (ISP) may blackhole all traffic to the targeted victim’s IP address, protecting itself and taking the target's site offline.
1. Reduce the total number of open DNS resolvers
An essential component of DNS amplification attacks is access to open DNS resolvers.
However, DNS resolvers should only provide their services to devices that originate within a trusted domain.
In reflection-based attacks, the open DNS resolvers will respond to queries from anywhere on the Internet, allowing the potential for exploitation.
So we can restrict a DNS resolver to only respond to queries from trustworthy sources.
2. Source IP verification – stop spoofed packets leaving the network
As the UDP requests being sent by the attacker’s botnet will have a source IP address spoofed to the victim’s IP address.
This is the key component that helps in reducing the effectiveness of UDP-based amplification attacks is for Internet service providers (ISPs) to reject any internal traffic with spoofed IP addresses.
If a packet is being sent from inside the network with a source address of this kind is dropped.
3. Disabling Recursion on Authoritative Name Servers
Systems do not need to support recursive resolution of other domains on behalf of a client and should be configured after disabling recursion.
Bind9
Add the following to the global options:
options {
allow-query-cache { none; };
recursion no;
};Microsoft DNS Server
In the Microsoft DNS console tool:
a. First, right-click the DNS server and click Properties.
b. After that click the Advanced tab.
c. Finally, in Server options, select the “Disable recursion” check box and then click OK.
4. Use a DNS-aware firewall.
We can use a DNS-aware firewall to only allow DNS responses into the network that match requests sent from local DNS servers.
5. Use DNS Anycast
A DNS Anycast will help to distribute traffic and avoid overloading any single DNS server.
6. Using third-party DDoS protection.
We can use any third-party DDoS protection like a scrubbing service.
7. Limiting Recursion to Authorized Clients
For DNS servers that are deployed within an organization or Internet Service Provider, the resolver should be configured to perform recursive queries on behalf of authorized clients only.
BIND9
In the global options, include the following:
acl corpnets { 192.x.x.x/24; 192.x.x.x/24; };
options {
allow-query { any; };
allow-recursion { corpnets; };
};Microsoft DNS Server
It is not currently possible to restrict recursive DNS requests to a particular client address range in Microsoft DNS Server.
8. Response Rate Limiting (RRL)
There is currently an experimental feature available as a set of patches for BIND9 that allows an administrator to limit the maximum number of responses per second from being sent to one client from the name server.
BIND9
On BIND9 implementation running the RRL patches, include the following lines to the options block of the authoritative views:
rate-limit {
responses-per-second 5;
window 5;
};Microsoft DNS Server
In Windows Server 2016, the Set-DnsServerResponseRateLimiting cmdlet enables RRL with default settings.
[Need assistance to mitigate DDoS attack? We are happy to help you! ]
Conclusion
This article will guide you on different methods to mitigate DNS amplification attack. Basically, DDoS attacks can really freeze websites or even cause server downtime.
DNS flood is a type of Distributed Denial of Service (#DDoS) attack in which the attacker targets one or more Domain Name System (DNS) servers belonging to a given zone, attempting to hamper resolution of resource records of that zone and its sub-zones.
A Domain Name Server (#DNS) Amplification attack is a popular form of Distributed Denial of Service (DDoS), in which attackers use publically accessible open DNS servers to flood a target system with DNS response traffic.
1. UDP reflection attacks exploit the fact that UDP is a stateless protocol.
2. An attacker then sends the UDP packet containing the spoofed source IP to an intermediate server.
3. The server is tricked into sending its UDP response packets to the targeted victim IP rather than back to the attacker's IP address.
This article will guide you on different methods to mitigate DNS amplification attack. Basically, DDoS attacks can really freeze websites or even cause server downtime.
DNS flood is a type of Distributed Denial of Service (#DDoS) attack in which the attacker targets one or more Domain Name System (DNS) servers belonging to a given zone, attempting to hamper resolution of resource records of that zone and its sub-zones.
A Domain Name Server (#DNS) Amplification attack is a popular form of Distributed Denial of Service (DDoS), in which attackers use publically accessible open DNS servers to flood a target system with DNS response traffic.
1. UDP reflection attacks exploit the fact that UDP is a stateless protocol.
2. An attacker then sends the UDP packet containing the spoofed source IP to an intermediate server.
3. The server is tricked into sending its UDP response packets to the targeted victim IP rather than back to the attacker's IP address.