Nagios NDOUtils Message Queue Exceeded – Fix it Now
This article covers how to resolve the Nagios error, NDOUtils: Message Queue Exceeded error occurs when the amount of messages increases.
NDOUtils uses the operating system kernel message queue. As the amount of messages increases the kernel settings need to be tuned to allow more messages to be queued and processed.
A flood of messages in the /var/log/messages related to ndo2db like:
ndo2db: Error: max retries exceeded sending message to queue. Kernel queue parameters may neeed to be tuned. See README.
ndo2db: Warning: queue send error, retrying... Nature of this Nagios error:
In Nagios you experience the following symptoms:
1. Missing hosts or services or status data
2. Takes a very long time to restart the Nagios process
3. Unusually high CPU load
How to fix Nagios error, NDOUtils: Message Queue Exceeded ?
The following commands are for the msgmni option.
For the grep command you executed previously:
i. If it did not return output, this command will add the setting to the /etc/sysctl.conf file:
$ echo 'kernel.msgmni = 512000' >> /etc/sysctl.conf2. If it did return output, this command will update the setting in the /etc/sysctl.conf file:
$ sed -i 's/^kernel\.msgmni.*/kernel\.msgmni = 512000/g' /etc/sysctl.conf3. After making those changes, execute the following command:
$ sysctl -p4. You need to restart services using the commands below:
$ systemctl stop nagios.service
$ systemctl restart ndo2db.service
$ systemctl start nagios.service
Manage Transaction Log File during Data Load - Do it Now
This article covers how to manage transaction log files in SQL Server for our customers. A transaction log is a file – integral part of every SQL Server database. It contains log records produced during the logging process in a SQL Server database.
The transaction log is the most important component of a SQL Server database when it comes to the disaster recovery – however, it must be uncorrupted.
The only way to truncate the log, so the space can be reused, is to perform a SQL transaction log backup. Therefore the most common reason for a transaction log file to have grown extremely large is because the database is in the FULL recovery model and LOG backups haven't been taken for a long time.
How do I stop a transaction log from filling up?
1. To keep the log from filling up again, schedule log backups frequently.
2. When the recovery mode for a database is set to Full, then a transaction log backup job must be created in addition to backing up the database itself.
To fix a transaction log for a database is full:
1. Backing up the log.
2. Freeing disk space so that the log can automatically grow.
3. Moving the log file to a disk drive with sufficient space.
4. Increasing the size of a log file.
5. Adding a log file on a different disk.
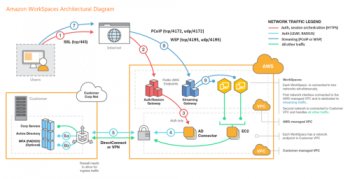
Set Up Amazon WorkSpaces - Step by Step Process
This article covers how to set up Amazon WorkSpaces for our customers. Amazon WorkSpaces is a managed, secure Desktop-as-a-Service (DaaS) solution. With Amazon WorkSpaces, your users get a fast, responsive desktop of their choice that they can access anywhere, anytime, from any supported device.
With Amazon WorkSpaces, you can provision virtual, cloud-based Microsoft Windows or Amazon Linux desktops for your users, known as WorkSpaces.
Generally, Workspaces are meant to reduce clutter and make the desktop easier to navigate. Workspaces can be used to organize your work. For example, you could have all your communication windows, such as e-mail and your chat program, on one workspace, and the work you are doing on a different workspace.
The Amazon WorkSpaces Free Tier provides two Standard bundle WorkSpaces with 80 GB Root and 50 GB User volumes, running in AutoStop mode, for up to 40 hours of combined use per month, for two calendar months, from the time you create your first WorkSpace.
Key Features of Amazon WorkSpaces:
1. The end-users can access the documents, applications, and resources using devices of their choice such as laptops, iPad, Kindle.
2. Network Health Check-Up verifies if the network and Internet connections are working. Also, checks if WorkSpaces and their associated registration services are accessible, and checks if port 4172 is open for UDP and TCP access or not.
3. Client Reconnect feature allows the users to access their WorkSpace without entering their credentials every time when they disconnect.
4. Auto Resume Session feature allows the client to resume a session that gets disconnected due to any reason in network connectivity within 20 minutes by default. This can be extended for 4 hours. However, the users can disable this feature any time in the group policy section.
5. Console Search feature allows Administrators to search for WorkSpaces by their user name, bundle type, or directory.
Some AWS Limitations:
1. AWS service limits. AWS service limits are set by the platform.
2. Technology limitations. An exceptional characteristic of this limiting factor is that it can be applied to all Cloud services, not just on AWS.
3. Lack of relevant knowledge by your team.
4. Technical support fee.
5. General Cloud Computing issues.
Setup and Configure tmpmail - Step by Step Process
This article covers method to Setup and Configure tmpmail.
Basically, tmpmail is a handy utility for CLI warriors within the command line.
By default, email addresses are created at random unless a specific email address follows the --generate flag.
Currently, w3m renders the emails in an HTML format within the terminal. If preferred, a user can use a GUI or text-based browser to view the email by passing the --browser flag followed by the command needed to launch the web browser of your choice.
TEMP-MAIL does not store your IP-address. This means you are reliably protected from all unauthorized actions that may endanger your information and compromise your privacy. All emails and data temporarily stored on our service are permanently deleted after the time expired.
How to install tmpmail ?
1. To install tmpmail, we can use the wget command or curl command to download the script from GitHub.
Next, open a terminal and then copy or type in the following command:
# wget https://raw.githubusercontent.com/sdushantha/tmpmail/master/tmpmail2. Now, run the chmod command against the script to modify the permissions, so the file is executable.
[root@host2 ~]# chmod -v +x tmpmail3. Next, we will move the file to a location somewhere in our $PATH. Use the following command to accomplish this.
# mv tmpmail /bin/
# which tmpmail
/usr/bin/tmpmailTo Generate a New tmpmail Address:
To create a new temporary email address, run the following command.
# tmpmail --generate
WDS deployment in Virtual machines – Few test cases
This article covers some methods to test Windows deployment in virtual machines. Windows Deployment Services (WDS) enables you to deploy Windows operating systems over the network, which means that you do not have to install each operating system directly from a CD or DVD.
To install Windows Deployment Services:
Windows Deployment Services ships as an innate role of Windows Server. I will be demonstrating on WS2016. All currently-supported versions provide it and you follow nearly the same process on each of them.
1. Start in Server Manager. Use the Add roles and features link on the main page (Dashboard) or on the Manage drop-down.
2. Click Next on the introductory page.
3. Choose Role-based or feature-based installation.
4. On the assumption that you're running locally, you'll only have a single server to choose from. If you've added others, choose accordingly.
5. Check Windows Deployment Services.
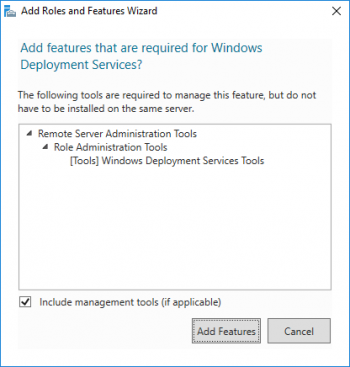
6. Immediately upon selecting Windows Deployment Services, you’ll be asked if you’d like to include the management tools. Unless you will always manage from another server, leave the box checked and click Add Features.
7. Click Next on the Select server roles page and then click Next on the Select server features page (unless you wish to pick other things; no others are needed for this walkthrough).
8. You'll receive another informational screen explaining that WDS requires further configuration for successful operation. Read through for your own edification. You can use the mentioned command line tools if you like, but that won't be necessary.
9. You will be asked to select the components to install. Leave both Deployment Server and Transport Server checked.
10. Click Install on the final screen and wait for the installation to finish.
To create WDS Boot Images:
When a system starts up and PXE directs it to the WDS server, it first receives a boot image. The boot image should match the operating system it will deploy.
You can obtain one easily.
1. Find the DVD or ISO for the operating system that you want to install. Look in its Sources folder for a file named boot.wim.
2. On your WDS server, right-click the Boot Images node and click Add Boot Image.
3. On the first page of the wizard, browse to the image file. You can load it right off the DVD as it will be copied to the local storage that you picked when you configured WDS.
4. You’re given an opportunity to change the boot image’s name and description. I would take that opportunity, because the default Microsoft Windows Setup (x##) won’t tell you much when you have multiples.
5. You will then be presented with a confirmation screen. Clicking Next starts the file copy to the local source directory. After that completes, just click Finish.
Disable NetBIOS and LLMNR Protocols in Windows Using GPO - How to do it
This article covers how to disable NetBIOS and LLMNR Protocols for our customers. The broadcast protocols NetBIOS over TCP/IP and LLMNR are used in most modern networks only for compatibility with legacy Windows versions. Both protocols are susceptible to spoofing and MITM attacks.
In the Metasploit there are ready-made modules that allow you to easily exploit vulnerabilities in the broadcasting NetBIOS and LLMNR protocols to intercept user credentials in the local network (including NTLMv2 hashes).
To improve your network security, you need to disable these protocols on the domain network.
In the domain environment, LLMNR broadcasts can be disabled on computers and servers using Group Policy.
To do it:
1. Open the gpmc.msc, create a new GPO or edit an existing one that is applied to all workstations and servers;
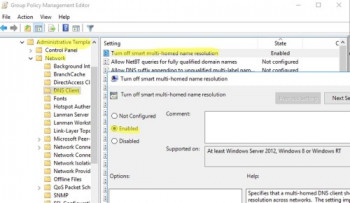
2. Go to Computer Configuration -> Administrative Templates -> Network -> DNS Client;
3. Enable Turn off smart multi-homed name resolution policy by changing its value to Enabled;
4. Wait while the GPO settings on clients are updated, or manually update them using the command: gpupdate /force.
To manually disable NetBIOS on Windows as follows:
1. Open network connection properties
2. Select TCP/IPv4 and open its properties
3. Click Advanced, then go to WINS tab and select Disable NetBIOS over TCP
4. Save the changes.